Friday Brief for 28 January 2022

Tech Terms
Boot Sequence — The initial series of processes a computer runs when starting up.
China’s Olympics App is Pure Spyware

What’s New: Cybersecurity researchers say the My2022 mobile app — the official app of the Beijing Winter Olympics — has serious security vulnerabilities and that “all Olympian audio is being collected, analyzed and saved on Chinese servers.”
Why This Matters: The Chinese government is mandating all Olympic athletes, coaches, and attendees use the My2022 app and, as of Thursday morning, the app is still available in the Apple and Android U.S. app stores where Americans can download it too.
Key Points:
The Chinese government says My2022 was developed by the Beijing Organizing Committee for the 2022 Olympics and records show that it is owned by the state-controlled Beijing Financial Holdings Group.
The app’s public capabilities include COVID-19 health monitoring, GPS navigation, and numerous tourism recommendations.
Citizen Lab researchers, however, demonstrate the app has a “devastating flaw where encryption protecting users’ voice audio and file transfers can be trivially sidestepped.”
Jonathan Scott, a mobile and IoT security researcher specializing in malware, spyware, and forensics, has also done a complete breakdown of the app and is raising alarms.
Of special concern is Scott’s discovery that My2022 is built using voice recognition and processing tech from iFLYTEK — a Chinese company that is blacklisted in the United States because of gross human rights violations.
iFLYTEK’s capabilities allow the app, according to Jonathan Scott, to conduct “continuous” voice monitoring.
What I’m Thinking:
No one should be surprised. Beijing has not been secretive about its desire to have and to use all data within its reach. For years, the Chinese government has enacted laws that ensure it has unfettered digital access and every Chinese company has been put on notice that anything less than full compliance with these government mandates will result in massive fines, executive imprisonment, and even being shut down completely. The only thing surprising here is that anyone believed the CCP would not want to strictly control the Winter Olympics and to seize the opportunity of hoovering up the deluge of data that will be created by the games.
This could/should have been avoided. Both Apple and Google will tell you they have thousands of app submissions to their stores everyday and that it’s impossible to do a deep-dive on every one of them. But, My2022 isn’t just another app — it’s an app developed by a state-run company, for the Chinese government, and mandated for every single Olympic participant. It collects tons of personal data and it should have been prioritized and examined with a fine-tooth comb. Even after outside researchers raised concerns about the app, it has remained in both companies’ app stores where Americans can download it, potentially compromising them as well. And even after the Citizen Lab report and the research by Jonathan Scott, the Apple app store still claims that the only data My2022 can connect to users is their contact information.
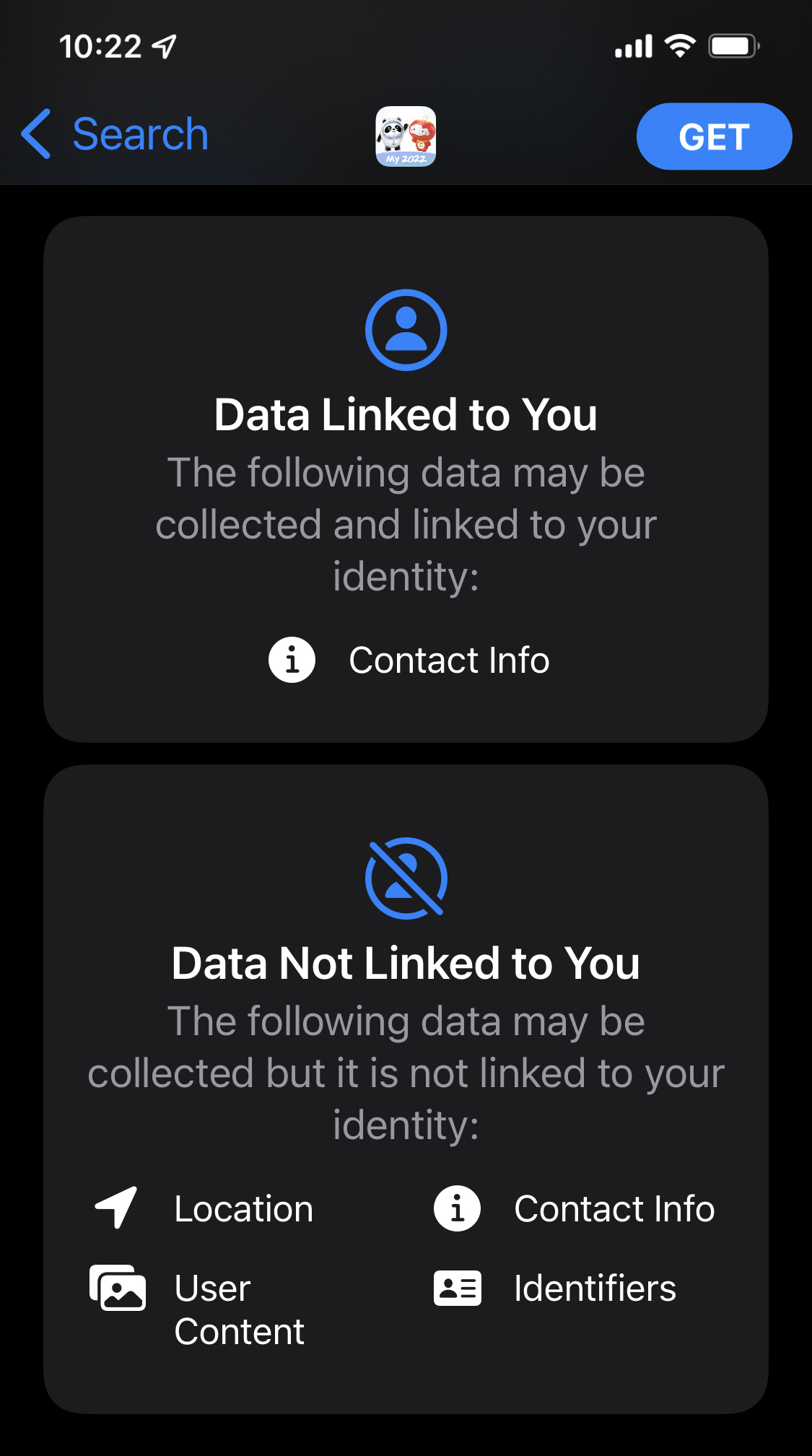
Capitulating to the Chinese invites U.S. regulations. The games in Beijing begin on February 4th. The day before, the U.S. Senate Judiciary Committee is scheduled to mark up the Open Apps Market Act — a bill that would require tech companies to relinquish control over how users add applications to their devices. I don’t like this bill and I’m on record explaining how laws like this would actually compromise our individual and corporate cybersecurity. But, failures like the My2022 app — especially if Apple and Google do not take decisive action before the games — completely undermine any assertion that these companies oppose opening up their app stores over security concerns. While I believe that capitulation to the CCP does not justify the United States cutting its own cybersecurity throat, there’s no denying that these companies are severely undermining their credibility. Apple and Google will need to explain themselves specifically, publicly, and convincingly if they want any hope of mitigating the justified frustrations of policy makers and the general public.
Preparing for Cyber Spillover from Ukraine
What’s New: As the situation along the Russia-Ukraine border continues to evolve, government officials and private sector leaders are preparing for possible cyber “spillover.”
Why This Matters: Previous Russian cyber operations that began in Ukraine have caused billions of dollars in damages around the world and the prospect of escalating hostilities in the region raises the specter of even more trouble to come.
Key Points:
The United States has responded in writing to Russia’s insane list of demands and, reportedly, Washington said, “Nah,” (though the U.S. letter has not been publicly released).
Meanwhile, Russian troops continue their “exercises” along Ukraine’s border with Russia and Belarus and the Biden administration is ordering more than 8,500 troops on alert for a rapid deployment to Europe.
Relatedly, the Department of Homeland Security issued a memo to law enforcement warning that Moscow may execute cyber attacks against the United States if things go sideways and CISA (DHS’s Cybersecurity and Infrastructure Security Agency) also warned American companies of these concerns.
A growing list of companies are reviewing their ties in Ukraine and those of their key vendors, according to the Wall Street Journal, as they seek to bolster their resilience to Russian attacks online.
“The worst-case scenario, cybersecurity experts warn, would be escalating breaches that mimic the 2017 NotPetya attack on a Ukrainian accounting firm that allowed hackers to rampage across other corporate networks, eventually causing an estimated $10 billion in global damage.”
What I’m Thinking:
This is getting serious. Last year’s Annual Threat Assessment by the ODNI states, “Russia continues to target critical infrastructure, including underwater cables and industrial control systems, in the United States and in allied and partner countries, as compromising such infrastructure improves—and in some cases can demonstrate—its ability to damage infrastructure during a crisis.” It also observes, “Russia almost certainly considers cyber attacks an acceptable option to deter adversaries, control escalation, and prosecute conflicts.” What does this mean? It means Moscow has the ability to execute devastating cyber attacks in the West and that we are entering a scenario where it might actually choose to do so. The actions of DHS/CISA and industry demonstrate such concerns are well-founded.
Spillover happens. Like a biological virus, digital viruses and other malware can be hard to contain. Interconnected networks and broadly deployed core hardware and software can allow an attack to quickly spread beyond its intended target(s). That means Russia could conduct an attack aimed squarely at Ukraine but its consequences could go well beyond that country — possibly pulling other nations into a conflict and climbing up the escalation ladder. If such spillover occurs, it will be doubly important that all involved watch their steps.
Synthetic Simulations of Tomorrow’s Realities
What’s New: Joe Robinson at Wired has an interesting article on how simulation tech can help predict the biggest threats.
Why This Matters: “Traditional analysis tools are poorly equipped to predict and respond to these blurred and intertwined threats,” says Robinson. “Instead, in 2022 governments and militaries will use sophisticated and credible real-life simulations, putting software at the heart of their decision-making and operating processes.”
Key Points:
The article cites the Brits’ development of a “digital backbone” for their Ministry of Defense that integrates cloud computing, advanced analytics and a new capability called Single Synthetic Environments (SSE).
SSEs leverage AI/Machine Learning, distributed systems, and cutting-edge modeling to make detailed simulations of the real world.
The idea, then, is that military strategists and warfighters can use these synthetic environments to predict, understand, and plan for future challenges.
“National security officials will be able to use SSEs to identify threats early, understand them better, explore their response options, and analyze the likely consequences of different actions. They will even be able to use them to train, rehearse, and implement their plans. By running thousands of simulated futures, senior leaders will be able to grapple with complex questions, refining policies and complex plans in a virtual world before implementing them in the real one.”
What I’m Thinking:
This stuff is real, but not quite ready for showtime. Robinson’s article is interesting and well worth the read. And, while SSEs and other advanced modeling capabilities continue to progress — I’m not as excited as the article suggests we should be. It’s true that these SSEs can be highly detailed and very useful generally; but to be an actual digital representation of the real world they require volumes of real-world data that we simply do not have. That’s not to say these tools have no utility or that they will never realize their full promise. As 5G and follow-on network upgrades enable a real internet-of-things, we’ll move closer to truly representative SSEs and that will be a massive improvement for everyone from military leaders to city planners. Until then, though, these models are still very much a work in progress.
Let’s Get Visual: The Top 10 Biggest Companies in India

Nerd Humor
Quick Clicks
That’s it for this Friday Brief. Thanks for reading, and if you think someone else would like this newsletter, please share it with your friends and followers. Have a great weekend!