Heads Up

I sat down with AEI’s big boss, Robert Doar, to chat about tech, culture, & national security. He asks me about "big tech", fake media, and Chinese aggression. You can listen to our conversation here.
Tech Terms
Air Gap — The physical separation or isolation of a system from other systems or networks.
Anticipating Russia’s Use of Cyber in Ukraine
What’s New: Russian President Vladimir Putin is positioned for a military invasion of Ukraine and cyber capabilities are likely to feature heavily in any future conflict.
Why This Matters: Russia has been hitting Ukraine with cyber attacks for years but we should expect a dramatic escalation of these efforts before and during a military incursion.
Key Points:
Dmitri Alperovitch — Co-Founder and former CTO of Crowdstrike and now Chairman of the Silverado Policy Accelerator — lays out one of the most compelling arguments I’ve seen on why Putin is likely to invade in the next few months. It’s worth reading the thread linked below.
Ever since Putin’s initial “annexation” of Crimea, Russian hackers have conducted a full-scale cyber campaign against targets in Ukraine’s political, economic, media, finance, and energy sectors.
On several occasions, hackers turned off electricity to hundreds of thousands of people for hours at a time.
In one of the most destructive cyber attacks ever, Moscow-backed attackers targeted Ukraine with the NotPetya virus, but it quickly spread beyond Ukraine causing billions of dollars of damage around the world — including in Russia.
Now the United States and Britain are helping Kyiv prepare for more cyber action by deploying various experts and defenses and, in the meantime, Moscow is turning up its online efforts — particularly digital disinformation.
What I’m Thinking:
Russia has established a strong digital foothold over the last eight years. Crimea’s annexation occurred in 2014. Ever since then, Moscow has been burrowing into and exploiting Ukraine’s networks and critical infrastructure. These operations have had at least three primary objectives. First, destabilize Ukraine’s government and foment popular unrest. Second, conduct persistent digital surveillance and reconnaissance. And finally, third, lay the digital foundation for future military operations by, for example, sabotaging critical infrastructure, infiltrating military command and control networks, and compromising key military capabilities like air defense systems. Putin’s intentions have been clear and he’s had plenty of time and opportunity to achieve these ends.
Everything starts in the “gray zone,” but will escalate quickly. As I’ve said, Russia has been cybering Ukraine for nearly a decade. Even so, if Putin decides to invade, all of these efforts will grow rapidly in both scale and severity. Propaganda will create a pretext for invasion. Critical infrastructure will be brought down. Digital denial and deception will be used to mask Russian operations and objectives. There may even be broader electronic warfare aimed at disabling Ukrainian access to communications, imagery, and GPS satellites. The bottom line is that all of this, and more, are within Russia’s capabilities and it is likely to be Russian decisions — not those of Kyiv — that set the conditions and scope of the coming conflict.
Hackers-For-Hire Industry Is Too Big To Fail
What’s New: Facebook parent company, Meta, has a new report detailing how “cyber mercenaries” targeted more than 50,000 of the social media platform’s users.
Why This Matters: While this newsletter and other sources have detailed the recent woes of NSO Group, the reality is that hacking- and surveillance-for-hire companies are booming.
Key Points:
If you don’t know about — or just want a quick refresher on — the drama around NSO, you can read my previous commentary here.
The Meta report says that, while most of these companies sell their wares under the guise of only targeting terrorists and criminals, the reality is much different.
“Our months-long investigation concluded that targeting is in fact indiscriminate and includes journalists, dissidents, critics of authoritarian regimes, families of opposition members and human rights activists.”
And Meta is naming names.
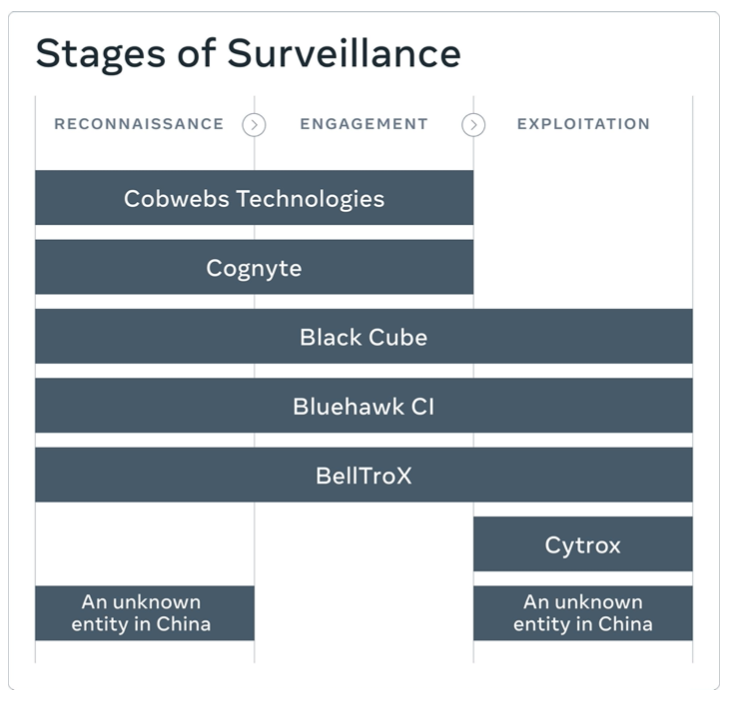
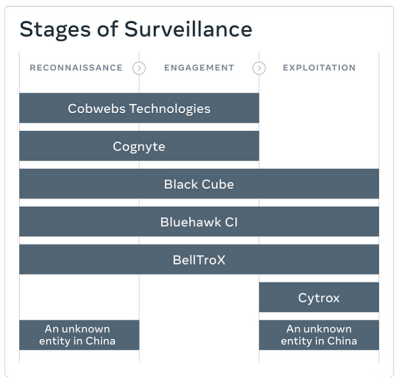
In addition to removing more than 1,500 accounts linked to these surveillance-for-hire groups, Meta also alerted approximately 50,000 people who the company says were targeted by these groups worldwide.
Interestingly, four out the seven groups identified by Meta — Cobwebs Technologies, Cognyte, Black Cube, and Bluehawk CI — are based in Israel.
What I’m Thinking:
This is big business. The general cybersecurity market is predicted to reach $345.4 billion by 2026. Hidden within this market is the hacking- and surveillance-for-hire market. As a point of reference, in 2019 NSO Group reported nearly $300 million in revenue.
Demand is only growing. Foreign governments are a key customer for cyber mercenaries. It’s a relatively cheap and fast way for smaller nations to gain access to world-class talent without all those pesky reporting and accountability challenges that come with official capabilities. But, global companies are also paying for these services. If you’re a U.S.-based, globally operating company, for example, you cannot conduct certain counter-hacking efforts or unilaterally retrieve stolen data and IP from an attacker’s networks. You depend on the U.S. government for justice and remediation. Or … you can pay foreign “cybersecurity consultants” to take “proactive measures” on your behalf. Certainly this brings its own risks, but it’s almost always faster and more efficient than waiting on Uncle Sam to defend your honor.
The connection to Israel isn’t a coincidence. Like NSO Group, it’s reasonable to believe Israel-based hacking companies need tacit approval from their government to export their capabilities and services. And the Israeli government has some understandable reasons for allowing this. First, Israel is a legit cyber powerhouse and allowing this surveillance market to grow will likely generate even greater wealth, insight, and capabilities. Second, by allowing these companies to work with governments like Saudi Arabia and the United Arab Emirates, they become a powerful diplomatic tool for normalizing relations and influencing key leaders. Finally, third, Israel has never been shy about spying on everyone — even its friends — and anyone who thinks they’re blushing about any of this is sorely mistaken. For sure, Israel’s aggressive use of cyber has real risks; but, the United States has also benefited from this forward-leaning posture and challenges like those demonstrated in the Meta report may simply be an unavoidable consequence of having these capabilities active at the cutting-edge (where we need them).
China Regulates Algorithms
What’s New: Beijing is cracking down on content management and recommendation algorithms.
Why This Matters: The Chinese Communist Party (CCP) wants to have decisive control over these society-shaping capabilities and these new rules will apply to Chinese companies everywhere and all foreign companies operating in China.
Key Points:
The Cyberspace Administration of China issued its Internet Information Service Algorithm Recommendation Management Regulations on Tuesday, saying the rules will come into force on March 1st.
The rules reportedly “standardize Internet information service algorithm recommendation activities, promote socialist core values, safeguard national security and social public interests, protect the legitimate rights and interests of citizens, legal persons and other organizations, and promote the healthy and orderly development of Internet information services.”1
Among the many requirements, anyone employing content management and recommendation algorithms must “actively spread positive energy,” not “induce users to set up addicted, over-consumption and other violations of laws,” and “regulate the development of Internet news information collection, editing and publishing services, reprinting services and dissemination platform services.”
The regulations’ lengthy “User Rights” section also demands service providers “provide users with options that are not specific to their personal characteristics, or provide users with convenient options to turn off algorithm recommendation services.”
There’s also this bit concerning security: “Algorithm recommendation service providers shall keep network logs in accordance with the law, cooperate with network information departments and relevant departments such as telecommunications, public security, and market supervision to carry out security assessment and supervision and inspection work, and provide necessary technical and data support and assistance.”
What I’m Thinking:
This is an authoritarian response to a universal challenge. The CCP is engaging powerful content management algorithms in a very totalitarian way. Specifically, the government is ensuring it holds the power and that “internet information services” are subservient to the state and know it. All of the bureaucratic requirements and labyrinthian language amount to a single outcome — any company using these algorithms must now do so only in a manner that the CCP finds acceptable and that facilitates government control over these algorithms and the data they utilize and generate.
This bad response doesn’t delegitimize the issue itself. It’s undeniable that algorithms play a huge role in what news users see, what products they purchase, and how they participate in modern society. In many ways, algorithms play an important role in allowing people to sort through the deluge of online content in a manner that maximizes satisfaction, ease, and even safety. But, it is also true that these algorithms often reinforce many of our worst inclinations and encourage a growing political tribalization. It’s completely legitimate for Americans to be concerned about and to debate these issues.
But China is no model for a free people. A number of the new Chinese provisions should sound familiar. Much of the language echoes proposals from draft legislation like the U.S. Filter Bubble Transparency Act, which, according to one of its sponsors, would require online platforms to offer their services “without being manipulated by secret algorithms driven by user-specific data.” While I can empathize with some of the underlying concerns, this approach — like that of the CCP — is misguided. I wrote at length on this topic for my friends over at the Dispatch (see the linked article below); but, the bottom line is that there is incontrovertible evidence that this approach leads to lower user satisfaction, higher volumes of extreme content, and more — not less — advertising revenue for the companies. The exact opposite outcomes proponents of such measures are looking for. While some will find Beijing’s “strong” response attractive, it proceeds from a theory of man and of government that is in direct contradiction with our most fundamental ideals and commitments. That’s not to say there’s nothing we can do about powerful algorithms; but, it is to say that there are a lot of things we shouldn’t do.
Let’s Get Visual
Nerd Humor

Quick Clicks
That’s it for this Friday Brief. Thanks for reading, and if you think someone else would like this newsletter, please share it with your friends and followers. Have a great weekend!
Translation provided by Google Translate.






Please note that we at The Dispatch hold ourselves, our work, and our commenters to a higher standard than other places on the internet. We welcome comments that foster genuine debate or discussion—including comments critical of us or our work—but responses that include ad hominem attacks on fellow Dispatch members or are intended to stoke fear and anger may be moderated.
With your membership, you only have the ability to comment on The Morning Dispatch articles. Consider upgrading to join the conversation everywhere.