DNI Issues 2021 Threat Assessment
What’s New: The Office of the Director of National Intelligence has issued this year’s Threat Assessment.
Why This Matters: The report candidly admits that, “The complexity of the threats, their intersections, and the potential for cascading events in an increasingly interconnected and mobile world create new challenges for the IC.”
Selected Key Points:
-
On emerging technologies:
“Following decades of investments and efforts by multiple countries that have increased their technological capability, US leadership in emerging technologies is increasingly challenged, primarily by China. We anticipate that with a more level playing field, new technological developments will increasingly emerge from multiple countries and with less warning … China stands out as the primary strategic competitor to the U.S. because it has a well-resourced and comprehensive strategy to acquire and use technology to advance its national goals, including technology transfers and intelligence gathering through a Military-Civil Fusion Policy and a National Intelligence Law requiring all Chinese entities to share technology and information with military, intelligence and security services … Moscow also views the development of advanced S&T as a national security priority and seeks to preserve its technological sovereignty. Russia is increasingly looking to talent recruitment and international scientific collaborations to advance domestic R&D efforts but resource constraints have forced it to focus indigenous R&D efforts on a few key technologies, such as military applications of AI.”
-
On Cyber:
“Although an increasing number of countries and nonstate actors have these capabilities, we remain most concerned about Russia, China, Iran, and North Korea. Many skilled foreign cybercriminals targeting the United States maintain mutually beneficial relationships with these and other countries that offer them safe haven or benefit from their activity … As states attempt more aggressive cyber operations, they are more likely to affect civilian populations and to embolden other states that seek similar outcomes … Authoritarian and illiberal regimes around the world will increasingly exploit digital tools to surveil their citizens, control free expression, and censor and manipulate information to maintain control over their populations.”
-
On China:
“The Chinese Communist Party (CCP) will continue its whole-of-government efforts to spread China’s influence, undercut that of the United States, drive wedges between Washington and its allies and partners, and foster new international norms that favor the authoritarian Chinese system … China will maintain its major innovation and industrial policies because Chinese leaders see this strategy as necessary to reduce dependence on foreign technologies, enable military advances, and sustain economic growth and thus ensure the CCP’s survival … We continue to assess that China can launch cyber attacks that, at a minimum, can cause localized, temporary disruptions to critical infrastructure within the United States.”
-
On Russia:
“Moscow will continue to employ a variety of tactics this year meant to undermine US influence, develop new international norms and partnerships, divide Western countries and weaken Western alliances, and demonstrate Russia’s ability to shape global events as a major player in a new multipolar international order … Russia continues to target critical infrastructure, including underwater cables and industrial control systems, in the United States and in allied and partner countries, as compromising such infrastructure improves—and in some cases can demonstrate—its ability to damage infrastructure during a crisis.”
What I’m Thinking:
-
I like this report. Every year I look forward to the Threat Assessment because it is the unclassified baseline on the most important challenges and threats. It’s a type of accountability for our national security enterprise in that it provides a history of how long we’ve known about problem, how we understand that problem, and how that problem has either grown or diminished over time. It’s a good read and I recommend it.
-
There’s a lot more in the report. I’ve only highlighted a few of the items most relevant to this newsletter. But, there is a great deal more on Iran, North Korea, COVID-19, ecological degradation, terrorism, transnational crime, and illicit drugs.
-
“Great Power Competition” is more than a catchy phrase. The fact that China is danger-close to rivaling the United States in some key economic, technological, and military spheres is not just an interesting anecdote; it is a development with significant consequences. Consequences so significant that we continue to struggle to accept them, let alone address them. For example, the report clearly states that “the CCP targets key technology sectors and proprietary commercial and military technology from US and allied companies and research institutions associated with defense, energy, finance, and other sectors,” and yet a 2019 Senate investigation found that over the last 20 years “China openly recruited U.S.-based researchers, scientists, and experts in the public and private sector,” and that “the federal government’s grant-making agencies did little to prevent this from happening, nor did the FBI and other federal agencies develop a coordinated response to mitigate the threat.” It does the nation no good to know about a threat and yet do nothing about it.
FBI Is “Hacking” Americans
What’s New: In what is understood to be an unprecedented move, the FBI has been “hacking” into computers that were compromised by the Hafnium Microsoft Exchange attack and removing the threat — without notifying the owners of these computers.
Why This Matters: “Today’s court-authorized removal of the malicious web shells demonstrates the Department’s commitment to disrupt hacking activity using all of our legal tools, not just prosecutions,” reads a statement from Assistant Attorney General John C. Demers, with the Justice Department’s National Security Division.
Key Points:
-
You’ll remember that it was recently discovered that the Chinese Hafnium hacking group compromised more than 400,000 Microsoft Exchange servers in 115 nations, including more than 30,000 in the United States.
-
When these networks were compromised, the attackers left “web shells” behind that would allow them (and others) persistent access in the future.
-
Now, according to The Washington Post, J. Edgar’s squad has used these same backdoors to remotely delete them.
“The FBI conducted the removal by issuing a command through the web shell to the server, which was designed to cause the server to delete only the web shell (identified by its unique file path),” explains the DOJ.
-
The DOJ statement indicates this operation may have affected “hundreds” of computers.
What I’m Thinking: I think I’m good with this. It definitely raises some questions about notification requirements; but, as I understand it, it was a remotely-executed command that did not require FBI presence on the network/computer itself. So this wasn’t a “search” warrant or other privacy-related action (but I’m no lawyer). They essentially did a “find and delete” for specific malicious files. It’s hard to argue against the efficiency of the move but it certainly pushes some boundaries. I will say there’s a bit of irony here when intelligence officials are pushing for mandatory disclosure laws.
Chips, Chips, Chips
What’s New: The CEO of Intel says it’ll take a couple of years to address semiconductor shortfalls, according to The Washington Post.
Why This Matters: Intel is the largest chip maker in the US, but building additional fabrication factories takes time. Meanwhile, consumer technologies, automakers, and other industries are being hammered.
Key Points:
-
Pat Gelsinger recently took over Intel and has been meeting with industry executives about how his company can ramp up chip manufacturing in the coming months.
-
Intel hopes to begin delivering extra chips within six to nine months.
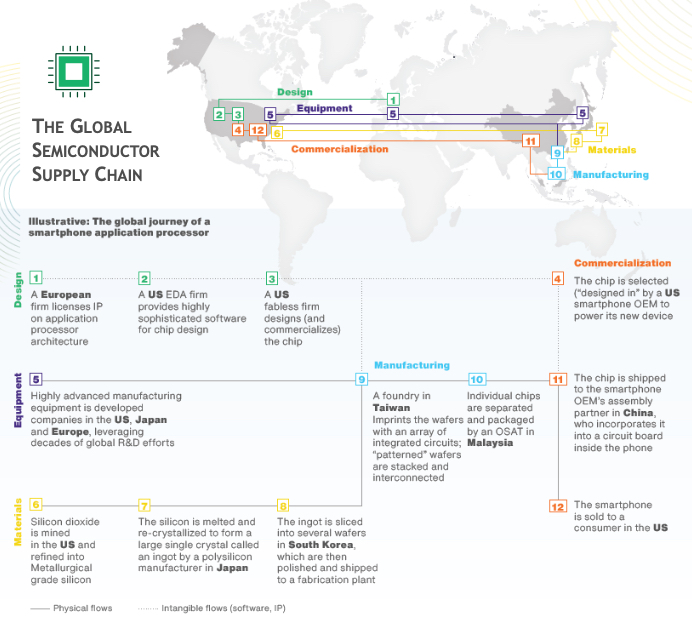
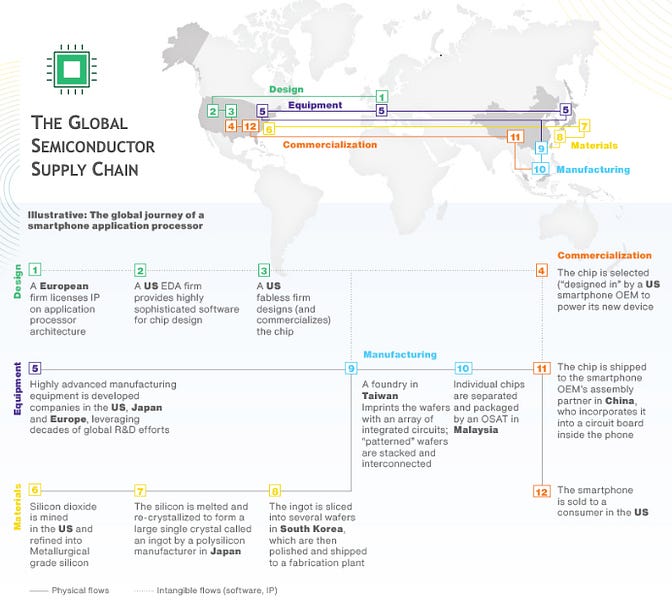
What I’m Thinking: Recently, I’ve been digging deeper into the global semiconductor supply chain. The following are a few facts I’ve found helpful1.
-
The US constitutes ~25% of global chip consumption — where the end users that purchase devices are — but drives 33% of chip demand — where the headquarters of the device maker is.
-
China is where 35% of chips are sent for device manufacturing/assembly, while 19% go to the US for this purpose.
-
10 of the top 20 chip design companies call the US home and more than 50% of the world’s chip designers are based in the US.
-
Chips were the 4th most traded product in the world in 2019, behind crude oil, refined oil, and automotive products.
-
The global chip supply chain has evolved with distinct geographic specialties — US leads in R&D while Asia leads in the most capital-intensive efforts (enabled in large part by government “incentives,” which drive 45-70% of the cost advantage).
Quick Clicks
That’s it for this Monday Brief. Thanks for reading, and if you think someone else would like this newsletter, please share it with your friends and followers. Have a great week!
Boston Consulting Group and Semiconductor Industry Association, Strengthening the Global Semiconductor Supply Chain in an Uncertain Era, Briefing, April 6, 2021.






Please note that we at The Dispatch hold ourselves, our work, and our commenters to a higher standard than other places on the internet. We welcome comments that foster genuine debate or discussion—including comments critical of us or our work—but responses that include ad hominem attacks on fellow Dispatch members or are intended to stoke fear and anger may be moderated.
With your membership, you only have the ability to comment on The Morning Dispatch articles. Consider upgrading to join the conversation everywhere.