Quick Note: It’s been a crazy couple of days so no audio version of the newsletter this week. Sorry about that, but I hope you’ll read-on and enjoy this week’s briefing.
Should the NSA Be Monitoring US Networks?
What’s New: In the wake of several major cybersecurity compromises, policymakers are considering new authorities that would allow the NSA to operate on American civilian networks.
Why This Matters: By law, the nation’s premier technical intelligence and cyber operations organization cannot operate on US networks and must only conduct its missions on foreign targets and networks.
Key Points:
-
CYBER Command (CYBERCOM) Director and Director of the NSA (DRNSA) Gen. Paul Nakasone told members of the Senate Armed Services Committee (SASC) that the US’s key challengers are taking advantage of legal prohibitions against domestic operations.
“They’re no longer just launching their attacks from different parts of the world. They understand that they come into the United States, use our infrastructure, and there’s a blind spot for us not being able to see them … What I am identifying right now is our adversaries understand that they can come into the United States and rapidly utilize an internet service provider, come up and do their activities, and take that down before a warrant can be issued, before we can have surveillance by a civilian authority here in the United States.”
-
Several SASC members on both sides of the aisle expressed a willingness to expand the NSA’s authorities and the Biden administration is reportedly already considering this approach as well.
-
Former NSA general counsel Glenn Gertstell told the Wall Street Journal that expanding the agency’s reach is long overdue:
“It can’t possibly be the case that the Fourth Amendment ties our hands in such a way that we just have to sit there and watch the Chinese romp through our infrastructure.”
-
But others, like SEN Ron Wyden, are understandably skeptical of this idea.
“The government already has the authority to watch every bit of data going in and out of federal networks … and NSA still missed the SolarWinds backdoor calling home for further instructions. The problem here isn’t our privacy laws, but that the government is failing cybersecurity 101. Some in the government now want to ask for new, warrantless surveillance of Americans’ communications to distract Congress from asking unpleasant questions about why [the Cyber Infrastructure Security Agency’s] $6 billion cyber shield failed to stop or detect the hacks.”
What I’m Thinking:
-
The challenge is real. It’s undeniable that laws preventing the NSA/CYBERCOM from operating on US networks does elevate the risk we accept in cyberspace. It is also demonstrably true that our most dangerous adversaries know about and exploit these limitations, with great impact on our national cybersecurity.
-
Concerns about expanded authorities are real too. For a number of reasons — some good, most bad — public confidence in our federal law enforcement and intelligence agencies is at an all time low. But even before this, the US constitution makes a deliberate choice to limit the federal government’s agility and capacity and gives preference to individual privacy and liberty — expressly motivated by a desire to constrain an all-knowing, all-powerful state.
-
Giving the NSA free-reign isn’t the right answer (I don’t think). The NSA is AWESOME at what it does, but giving them a “hall pass” on US networks won’t be enough to solve a problem of this scale. There’s just too much action on too many networks for even the “Puzzle Palace” to manage.
-
That doesn’t mean we can’t change some things. It’s probably time that we smoothed the way to temporarily bring in the NSA to help civilians during moments of crisis and in the wake of significant cyber attacks like the Holiday Bear and Microsoft Exchange operations. But, in what is well-covered ground in this newsletter, the best thing the federal government can do to protect domestic networks is LEAD. Uncle Sam needs to get its own house in order when it comes to federal networks and then be liberal in its sharing of intelligence, best practices, tools, and strategies with commercial operators. The government also needs to be crystal clear in telling industry where they think infosec resources should be invested and why. Industry doesn’t need a “leader,” but it craves leadership.
-
There’s no easy fix. The only way forward is a whole-of-nation, multi-year effort to change our INFOSEC fundamentals, in a context of aggressive coercive diplomacy targeting our key adversaries.
INTEL Wants to Build Chips for Others Too
What’s New: INTEL’s new CEO, Pat Gelsinger, says the company will outsource more of its chip production to third-party foundries; will invest $20 billion into two new fabrication factories (“fabs”) in the US; and will soon begin building chips for other companies.
Why This Matters: After a series of setbacks over the last five years, INTEL’s new CEO is signaling an aggressive effort to reassert the company’s core competencies and to expand into other critical semiconductor services.
Key Points:
-
INTEL is unveiling its “IDM 2.0” strategy that has three key parts.
-
First, it’s investing in its in-house chip design and manufacturing capabilities.
-
Second, it’s broadening its use of other chip fabricators like Samsung and TSMC.
-
Finally, third, it’s launching a new business called Intel Foundry Services that will directly compete with foreign fabs — particularly those in Asia.
-
Critical to this new effort is the fact that all of INTEL’s fabs will be located in the US and Europe — and therefore under less threat of compromise or coercion by China. Google, IBM, Microsoft, and Qualcomm have reportedly already agreed to partner with INTEL’s new fabrication services.
What I’m Thinking: This is good. I’m all for strengthening American semiconductor capacity for design and fabrication. Obviously, there’s a fair bit of showmanship here as the CEO of INTEL makes his mark; but, I’m fine with that so long as he follows through on the hype. Look, we’re a long way from being where we need to be in terms of domestic chip making capacity and supply chain resiliency. This is a good step forward and I wish INTEL (and their American partners) all the luck in the world.
Deep Dive: Navy Unveils “Unmanned Campaign Framework”
What’s New: The US Navy has released a new report on how it will leverage unmanned systems (UxS) in tomorrow’s naval operations.
Why This Matters: “The Department of the Navy’s unmanned campaign plan spans the entire doctrine, organization, training, material solutions, leadership and education, personnel, facilities and policy construct,” says Acting Secretary of the Navy Thomas W. Harker. “This document provides the overarching framework for the campaign plan, and is supported by detailed implementation plans at a higher classification.”
Key Points:
-
Why does the Navy want more and better UxS?
“The developing abilities of near-peer competitors drive the need for increased Naval capability distributed over a wider area … Autonomous systems provide additional warfighting capability and capacity to augment our traditional combatant force, allowing the option to take on greater operational risk while maintaining a tactical and strategic advantage … Unmanned systems will increase lethality, capacity, survivability, operational tempo, deterrence, and operational readiness.”
-
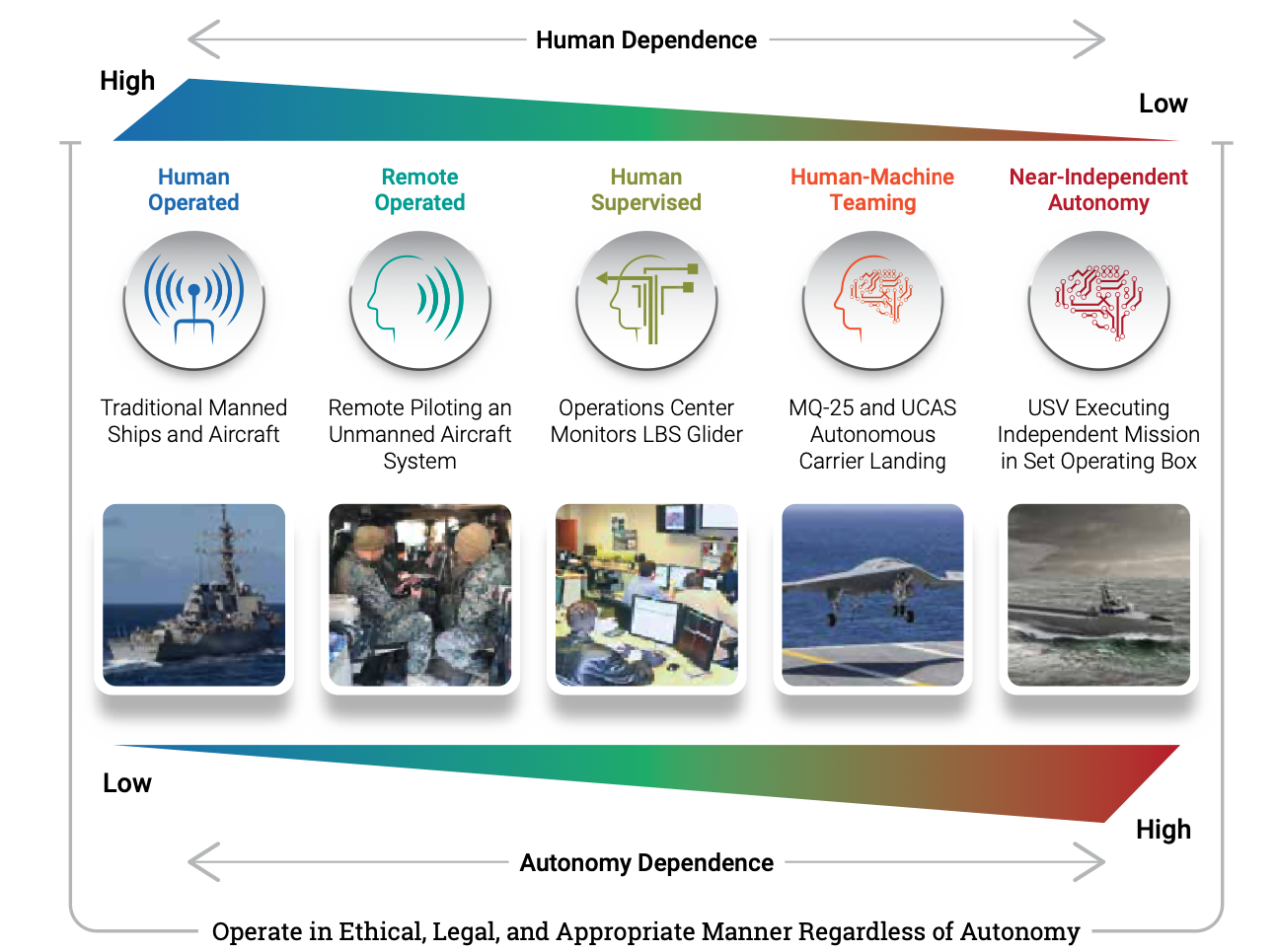
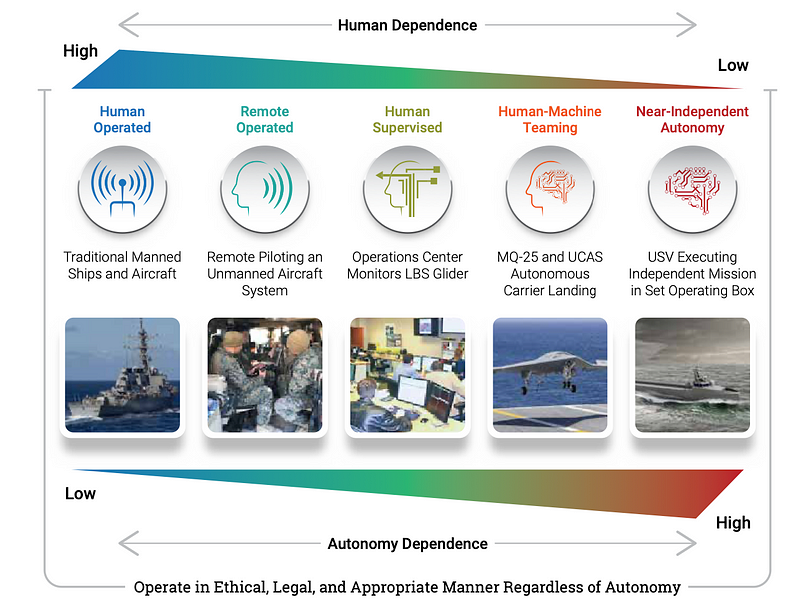
What, exactly, does the Navy mean by Uxs?
“The essence of unmanned is the physical removal or remote location of the human from the platform. Autonomy gives capable machines the ability to adapt interactively to the dynamic maritime environment … Different missions call for different amounts of human-machine interdependence. ‘Unmanned’ refers to the spectrum of autonomy from remote to autonomous and can be platform, system, or subsystem specific.
-
The campaign focuses on eight “functional areas” (language is taken directly from the report)
-
Platforms & Enablers: Requirements, resources and investment plans through development of a cross-domain capability-centric lens, addressing whole capability solutions that enable UxS to rapidly integrate across the Force.
-
Strategy, Concepts, & Analysis: Alignment of strategic priorities, connecting cycle of analytics and informing and reporting
on wargames, studies, exercises and experiments. -
Fleet Capability, Capacity, Readiness, & Wholeness: Derive employment plans, exercises and CONOPs to inform requirements applied to fleet issues regarding manning, training, and equipping the fleet.
-
RDT&E/Science & Technology: Identifying, informing, and integrating the Naval Research Enterprise on focused capability development, validation and insertion.
-
People, Education & Talent: Future personnel, talent recruitment and education necessary to field and sustain autonomous operations securely and reliably.
-
Logistics & Infrastructure: Ensuring the maintenance, sustainment, basing, and support of unmanned systems is understood and prepared to scale with the fleet.
-
Policy, Law, & Ethics: Addressing barriers, gaps, interpretations
and issues of policy that support the advancement and employment of autonomous solutions. -
Communication & Messaging: Collecting, consolidating and communicating the Naval narrative on unmanned systems. Ensuring one coherent voice and vision is shared across the DON when it comes to the future of UxS.
-
-
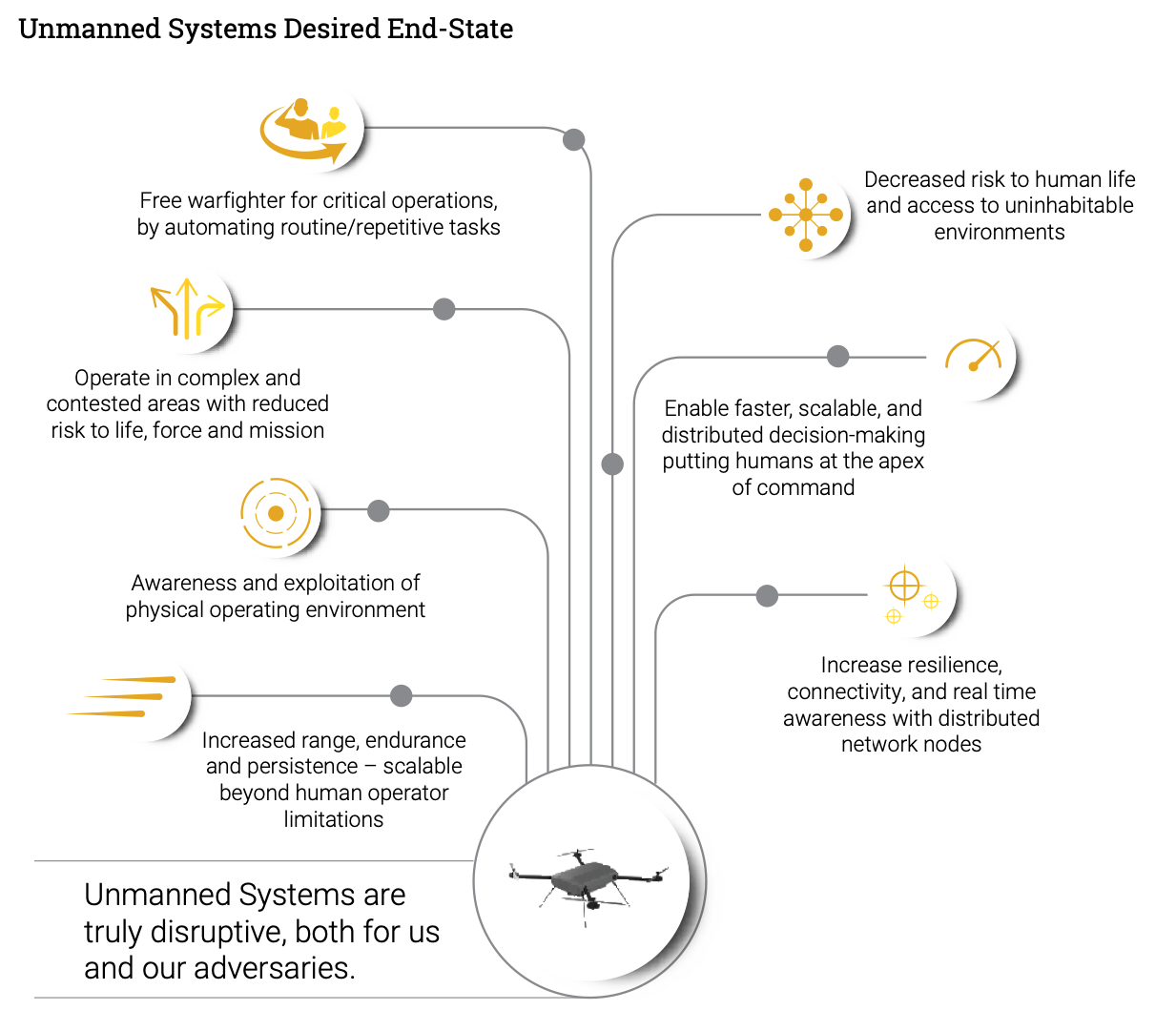
Ok, so what does the Navy want the future battlefield to be like?
-
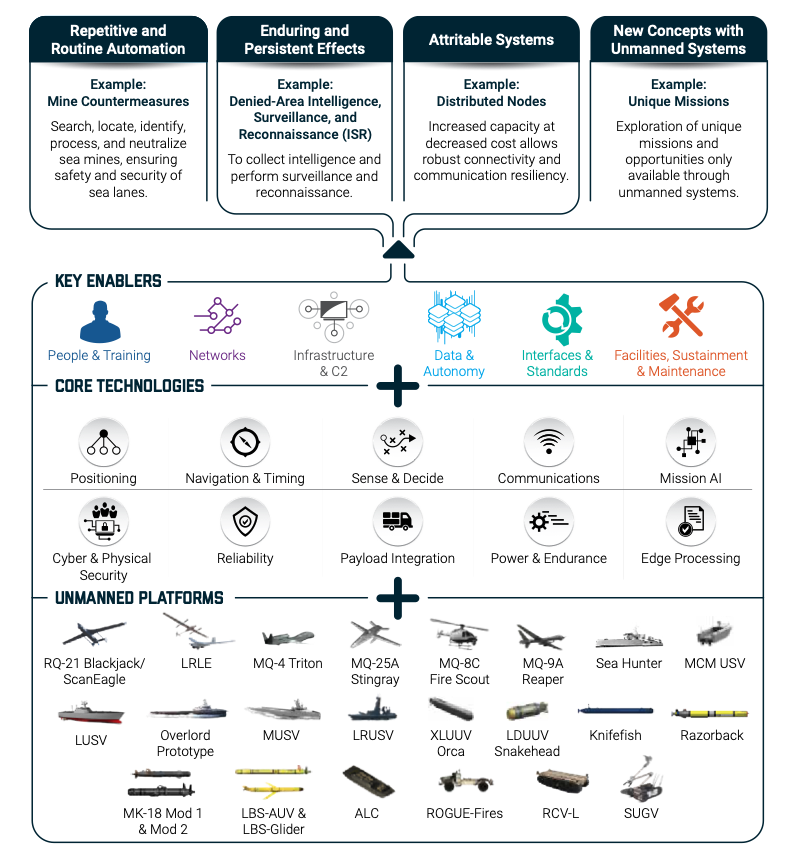
What’s the current UxS portfolio look like?
-
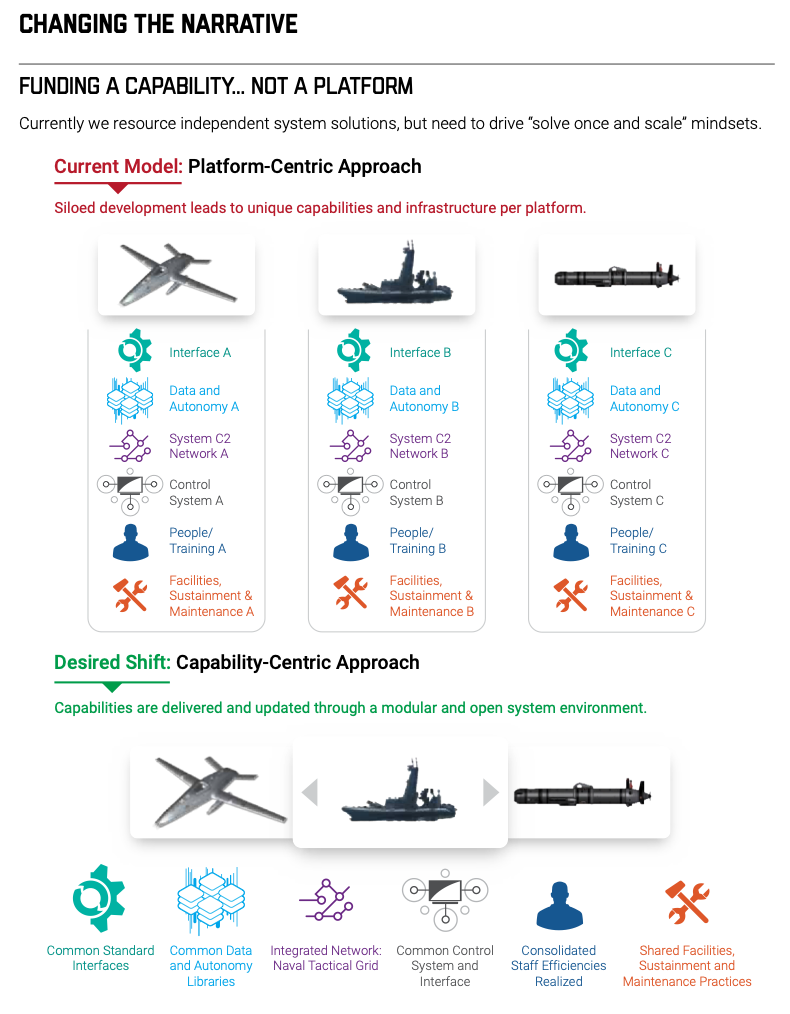
Ok, so what’s the big lesson of all of this for the future of Naval ops? Switching from a platform to a capability-centric approach.
-
Finally, what are the key barriers to success and how do we overcome them?

What I’m Thinking: I’ll be honest, I was pretty skeptical when I started reading this report; but, I think the Navy has done a good job defining the challenge and broadly mapping a way forward. Of course there’s tons of intangibles and anyone looking to make snarky remarks about another government “strategy” is going to find plenty of material in this report. Nevertheless, the Squids have locked onto one of the most important aspects of force modernization: focus on capabilities not platforms. This shift in focus does two things: (1) It helps avoid falling in love with specific systems and keeps the eyes on the actual capabilities that are needed to fight and win (which in turn encourages acquisition agility and cost effectiveness); and, (2) it encourages a diversity of the many supporting capabilities, technologies, and data sets that undergird critical capabilities by freeing them from a single platform.
Quick Clicks
-
The Dark Web is teeming with vaccine listings.
-
Group calls for ethical guidelines on location-tracking tech.
-
NFT Artwork by Sophia the robot sells for nearly $700K.
-
H&M is erased online after protesting Xinjiang cotton.
-
Microsoft may acquire Discord.
-
Here’s what tech CEOs wish they could say to Congress.
That’s it for this Monday Brief. Thanks for reading, and if you think someone else would like this week’s newsletter, please share it with your friends and followers.
Have a great week!






Please note that we at The Dispatch hold ourselves, our work, and our commenters to a higher standard than other places on the internet. We welcome comments that foster genuine debate or discussion—including comments critical of us or our work—but responses that include ad hominem attacks on fellow Dispatch members or are intended to stoke fear and anger may be moderated.
With your membership, you only have the ability to comment on The Morning Dispatch articles. Consider upgrading to join the conversation everywhere.