A Quick Note
Beginning today, the weekly Brief will be distributed on Fridays so that you can go into the weekend knowledgeable about the week’s key events (and also so that my wife doesn’t kill me for being in my study for most of the day on Saturday).
Tech Terms
Black Box AI (black·box) — Any artificial intelligence system whose inputs and operations are not visible to the user or another interested party.
Afghans Are Deleting Their Digital Lives
What’s New: Afghans are scrambling to erase pictures, videos, social media, and anything else that might invite Taliban attention.
Why This Matters: The new Taliban government is likely to use media stored on local devices, in private cloud accounts, and anywhere in between to identify and locate Afghans who worked with the coalition forces, the previous Afghan government/military, or is otherwise deemed a threat or target.
Key Points:
-
During the 20-year absence of the Taliban, Many Afghans embraced digital media as a way of recording, sharing, and enriching their lives. Now this media threatens to expose them to harassment, oppression, and death.
-
But the problem extends far beyond camera rolls, contacts, and social media posts — there are thousands of pictures on NGO websites featuring adults and children that could be used as evidence of “treason,” “sin,” or “apostasy.”
“The challenge is how do you balance getting information – like what’s going on at the airport, and people trying to reach you – with eliminating any evidence that a group would use to implicate you in something and take you round back to make an example of you,” says Welton Chang, chief technology officer at Human Rights First, a U.S. NGO focused on maintaining human rights.
-
In fact, the threat extends to the NGOs themselves. USAID has told its Afghan and other partners to scour their websites and social media in an effort to “remove photos and information that could make individuals or groups vulnerable.”
-
The Taliban has previously used data to find its “enemies,” including using a fingerprint scanner to identify Afghan military members (who they then killed) and Facebook to find anyone with long-standing relationships with the Afghan or American military.
-
It is possible that the Taliban has also gained access to a U.S. forces biometrics database, which again, would allow them to identify individuals of interest.
What I’m Thinking:
-
What a complete and total cluster. Here’s a list of five obvious actions that the U.S. government should have taken long before the U.S. pullout, but apparently did not.
-
Remove all digital files from American facilities and servers in Afghanistan that might be used to identify cooperative Afghans.
-
Destroy or otherwise render unusable all physical infrastructure used to house, transmit, or otherwise leverage this digital information — including servers, hard drives, biometric collection devices, and personal devices.
-
Work with social media and other tech companies to identify and warn Afghans using their platforms and services, providing them instruction on how to securely back up their information via cloud services (if desired) while deleting it from their devices and hiding it from the Taliban.
-
Work with relevant NGOs and other civil society entities to do the same.
-
Remotely secure (and if necessary, wipe) the networks and computers of the fallen Afghan government so that they cannot be used by Taliban.
-
-
We’ve made a bad situation even worse. As I’ve said before, the policy choice to leave Afghanistan is one that is reasonable and worthy of debate. What is inexcusable, however, is the President’s insistence that it be done in a manner and within a timeframe that guaranteed the chaos we are all now watching. Simply watch the linked video below and tell me if you think the President has fully grasped just how badly he’s screwed this up?
T-Mobile Hacked (Again)
What’s New: More than 40 million former, current, and prospective T-Mobile customers have had their data exposed in another cybersecurity failure by the telecommunications company.
Why This Matters: T-Mobile has disclosed at least five significant data breaches in the last four years and this latest breach is already getting Congressional attention.
Key Points:
-
According to a company statement, the stolen data includes names, birthdays, social security numbers, and driver’s license information.
-
The company, in an effort to assuage fears, also added, “no phone numbers, account numbers, PINs, passwords, or financial information were compromised.”
-
There have been a number of federal legislative proposals requiring private companies to report data losses like this, including this one from July, but none have become law. That doesn’t mean Congress won’t be talking about this breach.
Senator Ben Ray Luján (D-N.M.), who chairs the Senate’s Commerce subcommittee on communications, media, and broadband, told the Washington post, “Congress must review this incident that exposed millions of Americans and act to strengthen protections for consumers.”
What I’m Thinking:
-
This hack is bad; but, we’re used to “bad” and little is likely to change in the near-term. T-Mobile appears to have a real problem with cybersecurity and it doesn’t look like they’ve been willing to meaningfully address these issues. That said, data breaches like these are so common place and 40 million exposed individuals is in the low- to medium-range when it comes to the number of people affected. So, I’m not anticipating any significant legislation becoming law in the near-term.
-
The debate on data breach notification can be tricky. Many businesses oppose mandatory notification laws because they believe these would expose them to economic, legal, and reputational losses that could dwarf those caused by the data losses themselves — and they’re not wrong. Consumers, however, have a reasonable expectation to be protected from such losses and to be notified of their occurrence, because individuals also face economic, legal, and reputational risks when their data is stolen. While no federal notification law has been passed, several states have enacted mandatory disclosure, with California’s law often providing the broad outlines that are then tailored to meet specific state requirements. The National Conference of State Legislatures maintains a list of enacted and passed notification laws that can be reviewed here.
China Set to Pass Strict “Privacy” Law
What’s New: The National People’s Congress (NPC) is set to pass China’s first national privacy law, as a part of an ongoing crackdown on the nation’s technology giants, according to the Wall Street Journal.
Why This Matters: The legislation reportedly requires any individual or organization collecting or holding the data of Chinese citizens to obtain prior consent and to minimize their collection to only that which is necessary. Importantly, this law will not apply to or constrain the Chinese government.
Key Points:
-
Chinese regulators are in the midst of a growing effort to rein in tech companies who are increasingly seen abusive by the public and as a potential threat to power by the Chinese Communist Party (CCP).
“For China’s technology firms, the era of free data collection and usage in China—as in, free of responsibilities and at no cost—is over,” said Winston Ma, an adjunct professor at New York University’s School of Law, adding that the new law, combined with other regulations, will slow tech companies’ “unencumbered growth.”
-
In a bit of Orwellian double-speak, the draft law bars government collectors from gathering data beyond what is needed to perform “legally prescribed duties.” It just so happens that the CCP believes its government should have all data to perform its “duties.”
What I’m Thinking:
-
Obviously, the government is not going to be constrained. No matter what the draft bill says, the CCP is not limiting its access to Chinese data because such access is a prerequisite for its model of hyper-informed techno-totalitarianism. Any legislative language suggesting otherwise is either a ruse or will be removed from the final law.
-
The CCP is walking a tightrope. The Chinese government is concerned that its booming tech sector could challenge the CCP’s influence and control if it is not checked. This is why the CCP is taking a much harder line when it comes to issues like data security and antitrust. As it does this, however, the government risks decisively stalling the economic and technological engine driving the nation’s advancement.
-
This is also a bit of a show. Governments and consumers outside of China — particularly in the West — are getting wise to how Chinese companies (and therefore the Chinese government itself) hoovers up data and these governments and consumers are beginning to confront and stop this collection. I’m sure somewhere in the halls of the CCP headquarters some Party leaders are convinced this law will throw people like me off the scent. Not gonna happen.
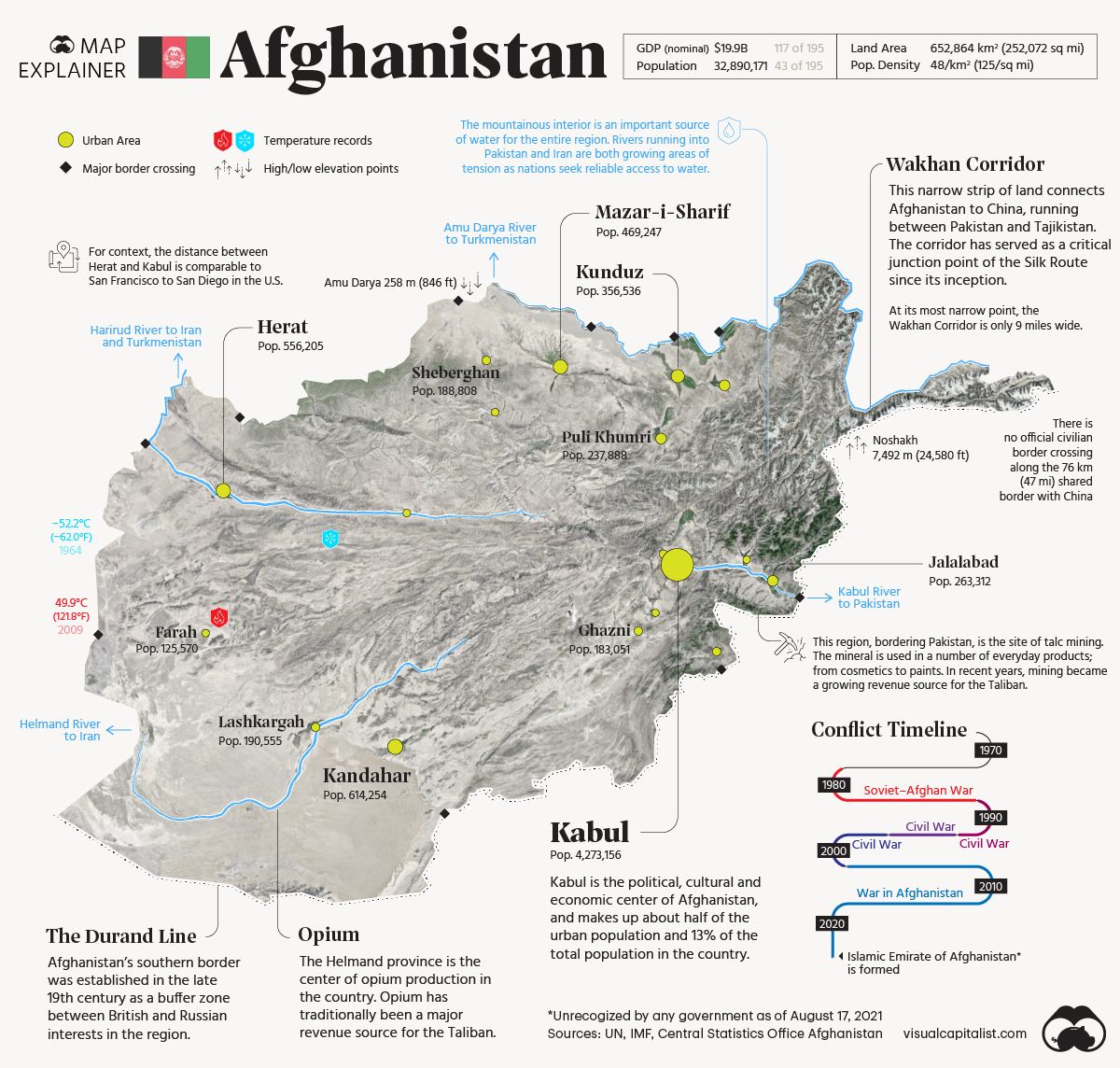
Let’s Get Visual
Nerd Humor

Quick Clicks
That’s it for this Friday Brief. Thanks for reading, and if you think someone else would like this newsletter, please share it with your friends and followers. Have a great weekend!






Please note that we at The Dispatch hold ourselves, our work, and our commenters to a higher standard than other places on the internet. We welcome comments that foster genuine debate or discussion—including comments critical of us or our work—but responses that include ad hominem attacks on fellow Dispatch members or are intended to stoke fear and anger may be moderated.
With your membership, you only have the ability to comment on The Morning Dispatch articles. Consider upgrading to join the conversation everywhere.