Twitter had a very, very bad day
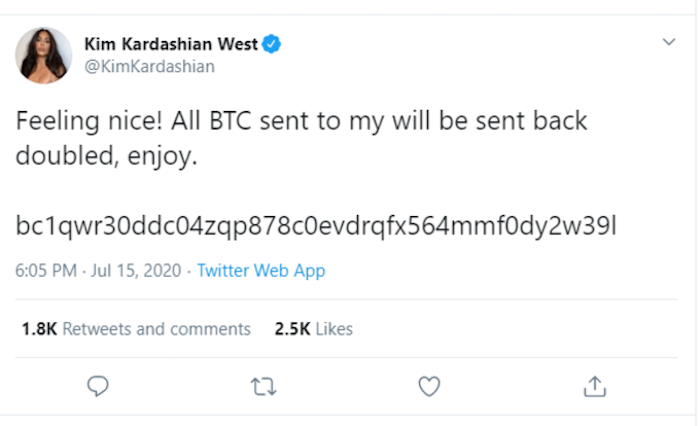
What’s new: A massive Twitter hack took over the accounts of celebrities, tech moguls, politicians, and companies, including Kim Kardashian, Kanye West, Bill Gates, Elon Musk, and Joe Biden. The hijacked accounts then asked millions of followers to send Bitcoin, promising to send back double the amount provided.
Why this matters: Honestly, it could have been much worse. The fact that the attackers used this massive breach to collect Bitcoin is kind of like stealing a Ferrari so that you can listen to the radio. Even if we dodged a bullet this time, the hack raises persistent questions about what and who we can trust online as we go into the hyper sensitive political atmosphere of the 2020 presidential election.
Twitter says that hack was made possible after a number of its employees fell victim to an organized social engineering scam that gave the attackers access to the social network’s internal management tools — constituting a massive security lapse on a platform populated by many of the world’s leading entertainers, politicians, and thinkers.
What we’re thinking: No matter how you slice it, this is a massive problem for Twitter and it’s not the first time. In August of last year, the Twitter account of company CEO Jack Dorsey was taken over even after the company had been warned about the vulnerability that allowed this to happen. Even more, the accounts that were hacked this week were “verified” accounts, meaning you’re supposed to be able to trust them.
So, to put it mildly, Twitter has a security problem.
That said, there are a lot of unknown details and we’ll have to wait to learn more. But, we can think of at least one way this might have happened.
Earlier this year, Vice reported on how so-called “SIM swappers” — hackers who gain access to a target’s information by taking over their phone accounts — were using social engineering and Remote Desktop Protocol (RDP) software to break into telecommunications companies, gain access to their internal tools, and then port a hacking target’s phone number to a phone the hackers control. Something similar may have happened with Twitter.
Here’s how it could have worked:
Bad guys start by targeting Twitter employees with social engineering scams so that they download or enable RDP software — software that allows someone to remotely access and control a user’s computer. (RDP software is commonly used by IT support staff to remotely monitor and service clients’ computers)
Once installed, the attackers used their access to leverage internal Twitter management tools to bypass two-factor authentication and other protections on the verified accounts. This theory would seem to fit with screen shots posted online of what appears to be a company software management tool. (These screenshots have been taken down.)
Having gained control, the attackers post messages from the accounts with a link to an anonymous Bitcoin wallet and then wait for the money to roll in. Which it did: $118K+
Again, we don’t have special knowledge of the attack. But, this is at least one way it might have happened. Even so, two-factor authentication is still important and you learn why by clicking here.
CIA given new freedom to operate online

What’s new: A new report says President Trump significantly expanded the CIA’s freedom to operate in cyberspace.
Why this matters: A 2018 presidential finding reportedly loosens the restrictions on what cyber operations Langley can conduct and who they can target. The new rules also allow the CIA to more quickly authorize its own covert cyber operations without getting White House approval.
Key points:
According to government officials interviewed in the article, the “very aggressive” finding “gave the agency very specific authorities to really take the fight offensively to a handful of adversarial countries.”
Russia, China, Iran, and North Korea appear to be specifically in view of the finding.
Of particular note, the finding is said to be less about intelligence collection and more about enabling offensive cyber attacks, like damaging an adversary’s critical infrastructure or other important networks.
Another key change includes lessening the evidentiary requirements for online operations against media organizations, charities, religious institutions, or businesses thought to be supporting foreign intelligence services, as well as individuals affiliated with these organizations.
What we’re thinking: It’s totally understandable if some of this makes you nervous. But, even with the undeniable risks, we think this is ultimately a good and necessary development.
This presidential finding is either the same finding that gives USCYBERCOM greater freedom to operate online or is directly related to it.
Even if the CIA has been given greater “freedom of movement” online, these activities fall well within the confines of covert action — meaning these activities can only be conducted under the CIA’s unique Title 50 authorities, they must be managed by the National Security Council and have specific objectives, and Congressional leaders must be notified and updated on these operations.
The reality is there is no risk-free option. Our adversaries are increasingly aggressive online and our national security enterprise must be free — under the proper oversight — to engage our enemies with the agility and aggression necessary to defend the nation and its people.
Russia trying to steal coronavirus vaccines
What’s new: Security officials say Russia’s intelligence services are trying to steal coronavirus vaccine research from labs in the US, Britain, and Canada, according to The Washington Post.
Why this matters: While this type of cyber espionage has become standard operating procedure for countries like Russia and China, it may also suggest Moscow is struggling to advance its own vaccine research.
The World Health Organization reports 160+ vaccines are being developed, with 23 having begun clinical trials in humans.
Russia is working on 26 different vaccines, but only two have advanced to human trials.
Key points:
Officials are pointing the finger at APT29 (AKA “Cozy Bear” or “the Dukes”), a group of hackers associated with Russia’s SVR, their version of the CIA.
APT29 was one of two Russian hacking groups who hacked the Democratic National Committee in 2016.
The Director of operations at the UK’s National Cyber Security Center (NCSC), Paul Chichester, urged labs around the world to take the threat seriously, saying, “We would urge organizations to familiarize themselves with the advice we have published to help defend their networks.”
Coronavirus surveillance is spreading too

What’s new: As the world continues to struggle with containing COVID-19, companies and other private sector actors are increasingly turning to bio-surveillance technologies.
Why this matters: Whatever the new “normal” is, it will almost assuredly involve a level of private sector monitoring that would have been unfathomable six months ago.
According to a Gartner data survey and Axios, 51% of employers are planning to collect temperature and other data on employees as they return to work.
60% are collecting self-reported data on symptoms with 25% also asking employees to report who they’ve been in contact with. 5% of firms say they’re going as far as collecting workers’ medical histories.
“We’re in this new era of biodata collection,” says Amy Webb of the Future Today Institute.
“I think most of it doesn’t have nefarious intent,” Webb says. “But, that being said, we don’t have clarity on how these data might be accessed by an insurer, for example. There isn’t enough regulation or transparency around where data are being stored.”
Temperature-reading infrared cameras are also gaining popularity when it comes to watching workers and customers.
“When the pandemic took hold, I started seeing more and more companies like Amazon using this technology to help identify sick people in their warehouses. Thermal imaging cameras are beginning to appear in Subway restaurants. Carnival Cruise Lines, whose ships became hot spots for the virus’ spread, said all passengers and crew would be screened when it began sailing again,” the New York Times’ Jonah Kessel writes.
And even remote employees are dealing with a rise in surveillance.
Since the start of the pandemic, according to NPR, employers are asking remote workers to install tracking software that monitors their online activities — including mouse movement and keystrokes — to ensure they’re being productive.
What we’re thinking: Yep, this is what life is going to look like for the foreseeable future. In addition to working with employees so that they don’t completely freak out, employers are also going to have to give very serious attention to how they secure the health data they collect and how they maintain transparency with customers and others whose data is deliberately or inadvertently hoovered up. Finally, it’s not just employers, schools are also getting into the bio-surveillance business.
UAE sending “Hope” to Mars

What’s new: The UAE plans to launch its “Hope” weather satellite on a mission to Mars next week.
Why this matters: If successful, this will be the Arab world’s first interplanetary mission.
The Hope probe is scheduled to orbit Mars for two years, collecting data and creating the first global map of Mars’ weather across all of its seasons.
It will take approximately seven months to reach Mars.
The launch is scheduled for some time between July 19-21 and can be watched live here.
New US moon suits get AI boost

What’s new: For the first time, critical components of NASA’s new space suit are being designed with AI, according to Wired.
Why this matters: AI algorithms are allowing engineers to design and organize critical life-support systems that are lighter and more efficient, yet still able to fit within tight weight and survivability standards for missions to the moon.
Key points:
NASA plans to return to the moon in 2024 in an effort to establish a permanent human presence there.
A part of this plan includes a new moon suit, revealed several months ago, called the Extravehicular Mobility Unit (xEMU) — the first major suit upgrade in nearly 40 years.
The xEMU allows astronauts significantly more mobility and comfort and also allows components to be swapped out for a more tailored fit.
“Squeezing more stuff into less space with reduced mass is the kind of complex optimization problem that aerospace engineers deal with all the time. But NASA wants boots on the moon by 2024, and meeting that aggressive timeline meant that engineers couldn’t spend weeks debating the ideal shape of each widget. Instead, they’re piloting a new AI-fueled design software that can rapidly come up with new component designs.”
“We consider AI to be a technology that can do something faster and better than a trained human can do,” says Jesse Coors-Blankenship, the vice president of technology at PTC, the American company that made the software. “Some of the software technologies are things engineers are already familiar with, like structural simulation and optimization. But with AI, we can do it faster.”
What we’re thinking: We want one.







Please note that we at The Dispatch hold ourselves, our work, and our commenters to a higher standard than other places on the internet. We welcome comments that foster genuine debate or discussion—including comments critical of us or our work—but responses that include ad hominem attacks on fellow Dispatch members or are intended to stoke fear and anger may be moderated.
With your membership, you only have the ability to comment on The Morning Dispatch articles. Consider upgrading to join the conversation everywhere.