DIA and the “Data Brokers”
What’s New: Senator Ron Wyden (D-OR) is drafting legislation to prohibit the federal government from purchasing American user data from so-called “data brokers.”
Why This Matters: It has been known for several years that the government occasionally purchases this information; however, the recent discovery that the Defense Intelligence Agency (DIA) is one of the entities acquiring this data is heightening concerns.
Key Points:
-
The Wall Street Journal previously reported federal agencies use cellphone location data for immigration enforcement.
-
In January, the DIA informed Sen. Wyden that it too purchases “geolocation metadata aggregated from smartphones.”
-
DIA says this data is “global in scope” but that “US location data points” are segregated in a separate database that can only be searched with “approval from the Office of the General Counsel (OGC), Office of Oversight and Compliance (OOC), and DIA senior leadership.”
-
DIA also says that it does not understand the Carpenter decision — a landmark Supreme Court ruling requiring the government to get a warrant before compelling phone companies to turnover geolocation data — to require the agency to get a warrant before purchasing this information.
-
The DIA also says it uses this information primarily to monitor for foreign threats to military forces stationed abroad. But Sen. Wyden isn’t buying it, saying, “The Fourth Amendment is not for sale,” and announcing his intention to legislate.
What I’m Thinking: Woo-boy, there’s a lot to this and I’m still noodling on it. But here are some initial thoughts:
-
The data at issue is clearly valuable and it’s not difficult to understand how it could facilitate intelligence generally, and DIA’s force protection mission specifically.
-
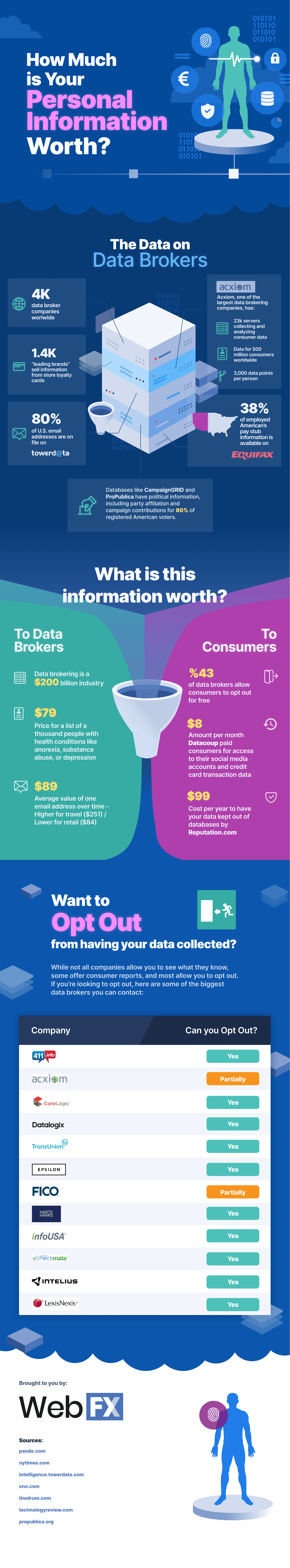
Americans freely, but sometimes ignorantly, turn over massive amounts of data to telephone companies, tech companies, and others in exchange for products and services. These companies then sell this information to data brokers, who in turn sell this data to other companies who use it to provide other products and services. All of this is legal and is spelled out within admittedly opaque terms of service agreements and other contracts.
-
This data provides anyone who has it with powerful insights into a user’s “pattern of life” — where a person lives, works, and shops; who they’re friends with; their online viewing habits; their politics; etc. (For example, see how the New York Times has used this information to track insurrectionists at the Capitol, children, and even the President)
-
I’m not a lawyer, but DIA’s rationale about Carpenter makes sense to me — they’re legally purchasing a legal service and not forcing telecoms to turn this data over — and the described protocols for protecting US persons data are similar to those used anytime this information is acquired by the intelligence community.
-
Having said that, privacy concerns around all of this are legitimate. And, if you’re not familiar with data brokers, you should know they are a $200 billion industry (see the infographic below for more) that could use more scrutiny.
-
Finally, it’s also important to know that, even if we block the federal government from purchasing and using this data, it is almost assuredly still being sold to foreign companies and governments, and that — I would argue — is of far greater concern and in need of remediation.
What’s in a Name? The Latest on SolarWinds
What’s New: It is now clear that what has been called the “SolarWinds” hack actually extends well beyond the SolarWinds company and its customers.
Why This Matters: Russian hackers were using multiple threat vectors in a campaign that is more comprehensive than previously thought and that will require a large intelligence effort to understand and to mitigate.
Key Points:
-
Private sector and government responders keep finding and pulling new cyber strings as they investigate the information security incident that was first publicly disclosed in December 2020.
-
Originally, it was believed the SolarWinds company was the center of gravity for the attack; however, that is now clearly not the case.
“…Approximately 30% of both private-sector and government victims linked to the campaign had no direct connection to SolarWinds,” according to Acting CISA Director Brandon Wales. “…This campaign should not be thought of as the SolarWinds campaign.”
-
Accordingly, I’m going to follow the lead of my friends Patrick Gray and Brett Winterford over at Srsly Risky Biz, and I will now refer to the attackers by the shorthand “Holiday Bear” and to the overall attack as the “HAND-WAVY” operation. (Don’t ask, just go with it.)
-
Importantly, Microsoft cloud services continue to feature heavily in the operation and may have even been the original vector that got SolarWinds owned.
-
You can read Microsoft’s latest update here.
What I’m Thinking:
-
The cybercraft is strong: The Russian hackers were patient and appear to have tailored their methods for almost every target — minimizing the risk of the whole op blowing up even if some intrusions were detected. It’s also not the case that every tool or trick that was used was earth-shattering or new; but, every part of the op appears to have been done with forethought and excellence.
-
Many hands make light work: The New York Times recently reported that US INTEL agencies are saying more than 1,000 Russian operators played a role in the hack. That’s a big number to swallow, but it could be true and would certainly match the emerging scope and scale of HAND-WAVY.
-
INTEL will play a critical role: Government and private-sector remediation efforts can provide a forensic view into all of this, but the US will likely need exquisite technical and human-enabled sources to get the full picture on (1) what was done, (2) how it was done, (3) for how long it was done, and (4) for what purpose(s) it was done.
-
An Inconvenient Truth: The facts that this operation went undetected for so long and that it was the private sector that alerted the government in the first place, suggests we don’t have the “exquisite” sources previously mentioned (otherwise we would have had some indications and warning), and that would mean we’re a long way from getting our arms around this.
-
Finally, normalizing this hurts our cause: It has become common for many in government — particularly those in the national security community — to say some version of, “Good on them and shame on us” when discussing state-backed cyber ops. Some have gone even further in the context of HAND-WAVY to minimize the attack by saying it looks like “traditional espionage.” This is a bad strategy because (1) in cyber, if you can observe you can attack and (2) because it immediately lessens the sense of risk and urgency, when that is the exact opposite of what we need to be doing.
The Cyber Dimensions of COVID-19 Vaccines
What’s New: From discovery to development to distribution, COVID-19 vaccines are proving to be a difficult cybersecurity challenge.
Why This Matters: Online threat actors can undermine public confidence in vaccines, inhibit their efficacy, and delay their distribution — all of which would extend the public health crisis.
Key Points:
-
From the very beginning, there have been concerns about foreign nations and other online actors stealing or manipulating vaccine development data.
-
Now that vaccines are actually rolling out, security experts are worried about defending the supply chains and hospitals that are delivering these meds.
“We need to think about how big this attack surface is — it’s just going to get bigger and bigger,” says Nick Rossman, global threat intelligence lead at IBM Security X-Force.
-
Hospitals and other healthcare targets are particularly under threat from ransomware and other attacks.
-
Since November, cyberattacks against healthcare targets are up 45% and these same targets accounted for nearly 80% of all data breaches in 2020, according to studies from Fortified Health Security and Check Point.
-
President Biden’s pandemic response plan tasks the Office of the Director of National Intelligence (ODNI) with an assessment of “ongoing cyber threats and foreign interference campaigns targeting COVID-19 vaccines and related public health efforts,” but a report about this threat is not a plan to stop it.
What I’m Thinking: The fact that most governments understand we’re all in this together is probably saving us a lot of trouble. Specifically, rational actors will understand that a decisive disruption of American vaccine efforts could disrupt vaccine development outside of the US by introducing doubt and instability into shared research datasets and strained supply chains for medical precursor materials.
But, it’s important to realize that these are not systemic defenses — they’re fortunate alignments of interests. Which means they are transitory. The systems and supply chains themselves are catastrophically vulnerable.
If a bad guy decides it’s in their interest to disrupt vaccine development and distribution — or if they decide they “just want to watch the world burn” — we’re all going to have a big problem on our hands.
That’s it for this Monday Brief. Thanks for reading, and if you think someone else would like this week’s newsletter, please share it with your friends and followers.
Have a great week!







Please note that we at The Dispatch hold ourselves, our work, and our commenters to a higher standard than other places on the internet. We welcome comments that foster genuine debate or discussion—including comments critical of us or our work—but responses that include ad hominem attacks on fellow Dispatch members or are intended to stoke fear and anger may be moderated.
With your membership, you only have the ability to comment on The Morning Dispatch articles. Consider upgrading to join the conversation everywhere.