
Tech Terms
Metaverse (met·a·verse) — a virtual-reality space in which users can interact with a computer-generated environment and other users.
Thoughts on the IC’s COVID Origins Report
What’s New: The U.S. Intelligence Community (IC) has released an unclassified summary of its assessment on the origins of COVID-19.
Why This Matters: “After examining all available intelligence reporting and other information … the IC remains divided on the most likely origin of COVID-19,” concludes the report.
Key Points (taken directly from the report):
-
All agencies assess that two hypotheses are plausible: natural exposure to an infected animal and a laboratory-associated incident.
-
Four IC elements and the National Intelligence Council assess with low confidence that the initial SARS-CoV-2 infection was most likely caused by natural exposure to an animal infected with it or a close progenitor virus—a virus that probably would be more than 99 percent similar to SARS-CoV-2
-
One IC element assesses with moderate confidence that the first human infection with SARS-CoV-2 most likely was the result of a laboratory-associated incident, probably involving experimentation, animal handling, or sampling by the Wuhan Institute of Virology.
-
Analysts at three IC elements remain unable to coalesce around either explanation without additional information, with some analysts favoring natural origin, others a laboratory origin, and some seeing the hypotheses as equally likely.
-
Variations in analytic views largely stem from differences in how agencies weigh intelligence reporting and scientific publications, and intelligence and scientific gaps.
-
The IC judges they will be unable to provide a more definitive explanation for the origin of COVID-19 unless new information allows them to determine the specific pathway for initial natural contact with an animal or to determine that a laboratory in Wuhan was handling SARS-CoV-2 or a close progenitor virus before COVID-19 emerged.
What I’m Thinking:
-
You have to understand how these assessments work. For these types of “community assessments,” standard operating procedure is for the Director of National Intelligence (DNI) to convene a group of analysts from all of the relevant intelligence agencies — typically under the auspices of the National Intelligence Council (NIC; pronounced “nick”)— granting them full access to all related intelligence and asking them to make a summary judgement based on the evidence. While a drive for consensus can occasionally water-down these assessments, in the post-9/11 and post-Iraq invasion world, analytic dissents between agencies is allowed and even encouraged.
-
You also have to understand that INTEL assessments aren’t opinion articles or “best guesses.” Policymakers make real policy based on what the IC tells them and the IC, therefore, has to be very clear about what it “knows,” what it “believes,” what it “suspects,” and what is “possible.” This is especially important in cases like this where, based on what the IC says, the U.S. diplomatic posture towards China could be decisively influenced. Most importantly, if you don’t know something, you say “I don’t know.” This is also why you have caveats like “low confidence” and “moderate confidence” in the report — to clearly make these delineations. Here’s a quick chart taken from a DNI Analytic Standards memorandum on how to interpret these qualifiers.
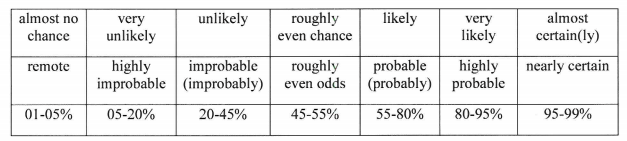
-
For some IC members, where you sit is where you stand. The divisions between IC elements are most likely a reflection of their own prioritization of intelligence emanating from their agency. The CIA, for example, will naturally give greater credence to human intelligence (HUMINT) or signals intelligence (SIGINT) that it has collected. Whereas, the State Department might not have the same confidence in this intelligence and may prioritize diplomatic reports. That’s not necessarily a reflection of pure parochialism, but simply of familiarity and general insight into the respective reporting sources.
-
Finally, China has the incentive and capability to “hide the ball.” The first, second, and third priority for the Chinese Communist Party (CCP) is its own power and survival. Obviously, the CCP doesn’t want the outside world to know China’s role in the global pandemic — whether it was malevolent or simply inept — because it will greatly complicate Beijing’s foreign policy. But it is equally important, perhaps even more important, that the Chinese people not be allowed to see any information that would suggest the CCP is not in complete control. The Chinese government was never going to cooperate with foreign investigations. In the context of the IC’s research into COVID-19’s origins, it is also true that our intelligence collection posture in China has been decimated over the last decade. Specifically, the illegal disclosures by Edward Snowden caused the CCP to double-down on securing the country against technical collection and the treason of former CIA officer Jerry Chun Shing Lee helped China to systematically dismantle our HUMINT networks there. This is the real reason the IC did not, and likely will not, give a definitive answer on the origins of COVID-19.
The Semiconductor Heist of the Century
What’s New: Dylan Patel over at SemiAnalysis has an excellent write-up of how China forced a British semiconductor company into a joint venture and then launched a Chinese competitor using stolen intellectual property.
Why This Matters: This is a case study in how the CCP uses coercive policies to pilfer foreign IP and to leverage this information for state interests.
Key Points:
-
As we’ve discussed at length in this newsletter, semiconductors are critical for technological development, production, and deployment.
-
The UK’s Arm Limited is one of the world’s most important semiconductor companies, with their IP shipping in billions of chips every year.
-
When the company was acquired by Japan’s SoftBank, they made a big push into the Chinese market — where they were forced into a joint-venture with a consortium of Chinese investors.
-
This consortium was given exclusive rights to distribute Arm IP in China.
-
Recently, however, this consortium — now called (Arm China; “安谋科技”) — announced that it would be rebranding its IP, developing this IP even further, and moving forward independently of SoftBank’s Arm Limited.
-
The full write-up is really good and I highly recommend giving it a read.
What I’m Thinking:
-
When you deal with the devil, you always get burned. The Chinese playbook is now well documented: (1) force a joint venture to get access to key IP; (2) steal all the IP you can; (3) use stolen IP to build a Chinese competitor to the suckers dumb enough to enter into a joint venture in the first place; and (4) run the foreign competitor out of the market by limiting their market share and preferencing the Chinese alternative.
-
This isn’t just embarrassing. While Arm and a host of other companies are rightly embarrassed by these developments, the problem is much bigger. It is arguable that this approach is netting more IP, trade secrets, and other critical information for the Chinese than traditional espionage ever will. Whole sectors of the Chinese tech economy — like semiconductors — are being largely built through these forced joint ventures and many of these sectors are critical for national security. As the old saying goes: “Fool me once, shame on you. Fool me twice, shame on me. Fool me three times, I’m an idiot.”

Feds Expanding Use of Facial Recognition Tech
What’s New: An internal poll of U.S. government agencies shows that many of them plan to expand their use of facial recognition technologies (FRTs) to look for criminals and to scan for threats, according to a GAO report.
Why This Matters: The departments of Agriculture, Commerce, Defense, Homeland Security, Health and Human Services, Interior, Justice, State, Treasury, and Veterans Affairs all said their facial recognition efforts will grow.
Key Points:
-
While public awareness of facial recognition is causing some angst, a Pew Poll in 2019 found that more than half of U.S. adults trust law enforcement with this technology, but are less comfortable with advertisers and tech companies using it.
-
Most of the agencies in the GAO report say they’ll grow their use of FRTs by 2023, primarily to enhance their respective homeland security and law enforcement missions.
-
In light of several high-profile examples of FRTs leading to wrongful arrests, multiple tech companies have suspended their FRT contracts with federal and local governments.
-
A previous GAO report said 20 federal agencies use or have developed facial recognition tech, but 13 of those same agencies said they did not “have awareness” of which private systems they used and had therefore “not fully assessed the potential risks … to privacy and accuracy.”
What I’m Thinking: Facial recognition tech is here to stay and many of its advantages are obvious — finding and tracking terrorists in a crowd, for example. But, these things are not ready for wide-scale deployment and, even more importantly, there is good reason to doubt the government’s capacity to secure this data in the first place. In light of this, Congress should take up the issue of privacy in the specific context of FRTs. We need a bill that debates and establishes what a reasonable expectation of privacy and security looks like in a world of ubiquitous public surveillance and identification.
Let’s Get Visual

“The SpaceX Starship might be the next rocket to take humans to the moon, but it won’t be the first, and likely not the last.
Starting in the mid-20th century, humanity has dedicated lots of time and resources to explore space. We’ve launched satellites, telescopes, space stations, and spacecrafts, all strapped to rocket-propelled launch vehicles that helped them breach our atmosphere.
This infographic from designer Tyler Skrabek stacks up the many different rockets of the world side-by-side, showing which country designed them, what years they were used, and what they (could) accomplish.”
Nerd Humor

Quick Clicks
That’s it for this Friday Brief. Thanks for reading, and if you think someone else would like this newsletter, please share it with your friends and followers. Have a great weekend!






Please note that we at The Dispatch hold ourselves, our work, and our commenters to a higher standard than other places on the internet. We welcome comments that foster genuine debate or discussion—including comments critical of us or our work—but responses that include ad hominem attacks on fellow Dispatch members or are intended to stoke fear and anger may be moderated.
With your membership, you only have the ability to comment on The Morning Dispatch articles. Consider upgrading to join the conversation everywhere.