Homeland Secretary Is Gonna Do “Sprints”
What’s New: DHS Secretary Alejandro Mayorkas says his agency will be launching a series of 60-day “sprints” focused on some of the nation’s top cybersecurity challenges.
Why This Matters: “Sprints” are common in the software development sector, where a dedicated effort is focused on a specific objective for a fixed period of time.
Key Points:
Mayorkas outlined this initiative during a speech last week hosted by the RSA conference.
He began by listing three “hard truths”:
“First, the government does not have the capacity to achieve our nation’s cyber resilience alone. So much of our critical infrastructure is in the private sector’s hands …
Second, our government got hacked last year and we didn’t know about it for months … This incident is one of many that underscores a need for the federal government to modernize cybersecurity defenses and deepen our partnerships.
Third, the government seeks to speak with one voice but too often we speak through different channels, which can confuse and distract those who need to act on our information and act fast.”
After that, he turned to the “sprints”:
“The first sprint will focus on the fight against ransomware, a particularly egregious type of malicious cyber activity that usually does not discriminate whom it targets. It is malicious code that infects and paralyzes computer systems until a ransom has been paid. Individuals, companies, schools, even hospitals and other critical infrastructure have been among the victims …
Closely related to this first sprint, is the second sprint focusing on the cybersecurity workforce. We cannot tackle ransomware and the broader cybersecurity challenges without talented and dedicated people who can help protect our schools, hospitals, critical infrastructure, and communities …
Later this summer, we will launch our third sprint focused on mobilizing action to improve the resilience of industrial control systems …
The last three sprints for the coming year will focus on better protecting our transportation systems, safeguarding election security, and advancing international capacity-building.”
What I’m Thinking: Everything the Secretary laid out is a legitimate “hard truth” and a worthy “sprint” challenge. Even more, it’s not hard to believe that the Holiday Bear operation (aka, SolarWinds) and the Hafnium Microsoft Exchange hack has decisively shaped DHS’s priorities. But there are systemic challenges that remain unaddressed and so it’s difficult for me to get too excited about all of this. Certainly there are some low-hanging-fruit opportunities to make things a little better and maybe these “sprints” will surface those opportunities. But that won’t solve the agency’s lack of authorities, resources, or expertise. Honestly, we’ve known about these “hard truths” for at least the last three administrations. What I’d like to hear instead is a concrete plan on how DHS (and the Biden administration more broadly) is going to address these realities and meaningfully change them. Until then, we’re trying to put out a house fire with Solo™ cups.
Biden Wants Billions for Grid Cybersecurity
What’s New: President Biden is calling for more than $100 billion in funding for overhauling the nation’s power grid as part of his proposed $2 trillion infrastructure plan.
Why This Matters: The nation’s electric grid is woefully vulnerable to cyberattacks and a significant portion of this money is reportedly aimed at building out grid resilience.
Key Points:
“Any infrastructure bill that doesn't include serious money for grid improvements and grid resilience will miss the objective of a resilient economy because the grid will remain vulnerable,” says Jim Cunningham, executive director of Protect Our Power, a nonprofit focused on grid security.
In 2019, 56% of utilities said they had faced cyberattacks in the last year (Klon’s comment: the other 44% simply didn’t know they had been attacked).
In that same year, the DNI testified before Congress that “Russia has the ability to execute cyber attacks in the United States — such as disrupting an electrical distribution network … [and is] mapping our critical infrastructure with the long-term goal of being able to cause substantial damage.”
Many US lawmakers got religion on this threat in 2018, after seeing Moscow wreak havoc on Ukraine’s critical infrastructure.
In response, we’ve upped our own operational tempo (OPTEMPO) against Russia’s grid, as way of signaling that things are getting real and that everybody needs to calm down.
What I’m Thinking:
Grid security is military security. The military relies on electric power for critical missions. But, the Pentagon has little-to-no control over sources of electrical power — most of the energy consumed by military installations comes from commercial power sources.
This is a big, complex challenge. More than 3,000 utilities provide power through 200,000 miles of high-voltage transmission lines; 55,000 substations; and more than 5 million miles of distribution lines. And all of these are ripe targets for disruption.
Security is about more than standards. There are good reasons to be skeptical of government engagement and funding for grid modernization. It’s also reasonable to argue that Washington should constrain itself to providing Critical Infrastructure Protection (CIP) standards and then leave utilities alone to meet these standards. Unfortunately, that isn’t working (somewhere between 10-20% of the grid meets these standards). The universal assessment of the entire US government for at least the last two decades is that our power grid is decisively vulnerable and that individual utilities lack the expertise and resources to adequately address these vulnerabilities. The threat is so severe that it, in my opinion, goes directly to the core constitutional requirement that the federal government provide for the “common defense.”
This doesn’t mean we need a government takeover. There is a middle ground between “total grid failure” and “total government takeover.” What we need is sensible partnerships between the government and private sectors that should likely include government assistance commensurate with the government’s equities that are bound up in the grid. Even so, this cannot be a bottomless or endless subsidy without clear deliverables, metrics, and accountability. But all of this is doable (and necessary). As a conservative, I have a healthy skepticism of most government engagement in the private sector. But, I try to avoid having a cynicism of government that would prevent me from securing the very things I’m trying to conserve.
Russia Targeted Cyber Threat Hunters
What’s New: The Russian operatives behind the Holiday Bear (aka SolarWinds) hack identified and targeted key individuals who would be responsible for responding to the attack, according to CNN.
Why This Matters: Government officials are expressing surprise at the level of “granular” knowledge Russia had, and was able to gain, about working-level cybersecurity personnel.
Key Points:
After gaining access to multiple US government agencies, including the Department of Homeland Security, the hackers identified a core group of security officials and analysts who would be among the first “threat hunters” to respond to the breach once it was discovered.
After identifying these individuals, the hackers attempted to compromise their targets’ emails and other credentials.
Then-Acting Secretary of Homeland Security Chad Wolf was one of those targets who was compromised.
"It appears as if the Russian SolarWinds hackers possess granular information on personnel and who among them is likely to be involved in investigating the SolarWinds hack," said Cedric Leighton, a former NSA official and CNN military analyst. "This could mean that networks have been penetrated to a degree we've not known before. If that's true, we need a complete housecleaning of all our defensive cyberoperations."
What I’m Thinking: This is important, but not surprising. Identifying likely first-responders to a cyber incident is standard operating procedure in modern cyber operations. This is done because (1) these individuals’ roles, access, and knowledge typically mark them as priority targets anyways and (2) keeping an eye on their emails and other communications provides attackers with a type of early-warning capability for when the hack has been discovered. In fact, Russia (and other nations) have likely compiled detailed lists of cybersecurity personnel across the government as a part of their routine intelligence collection. Even so, this is still significant in that it is another demonstration of how well this operation was executed and of how significant of a challenge we face.
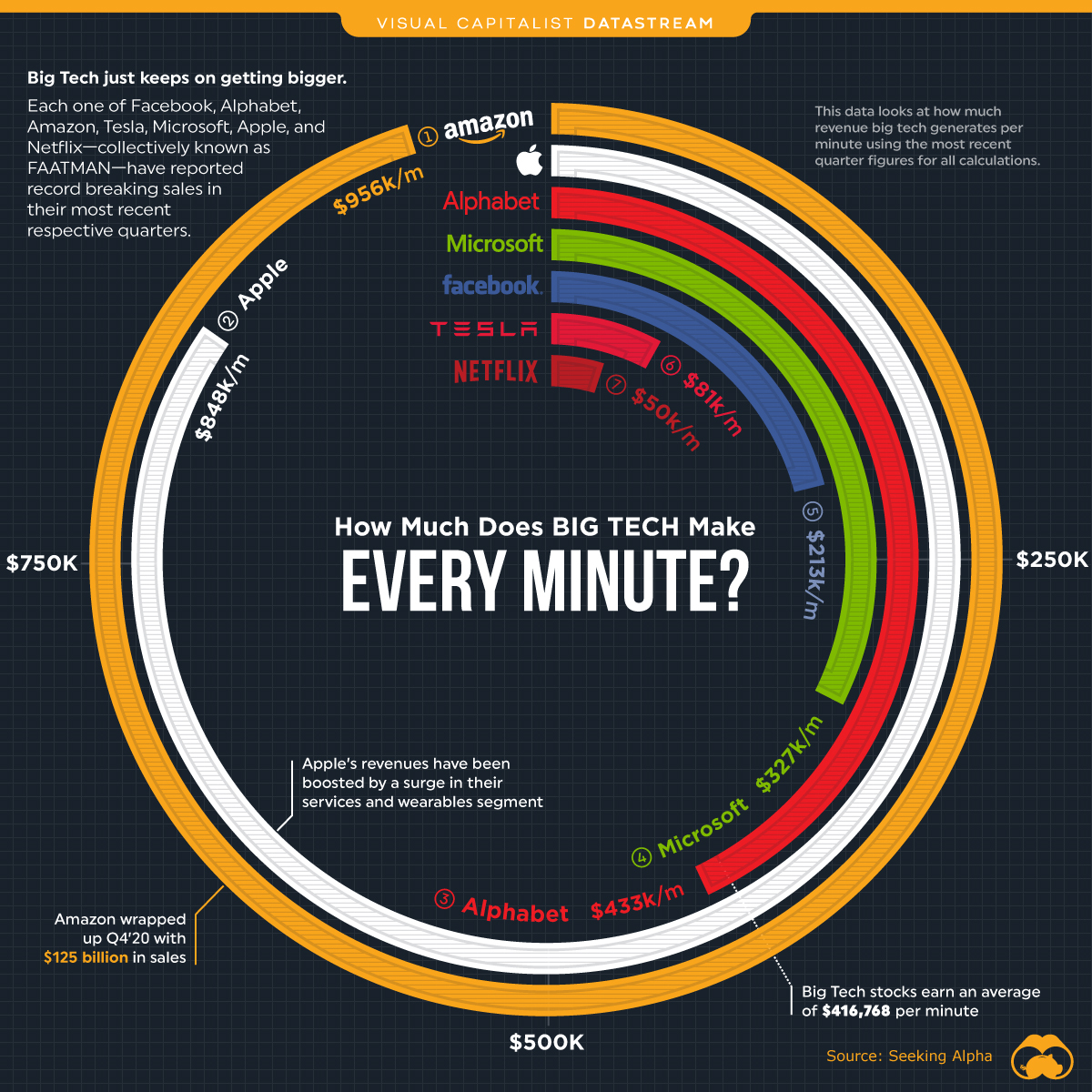
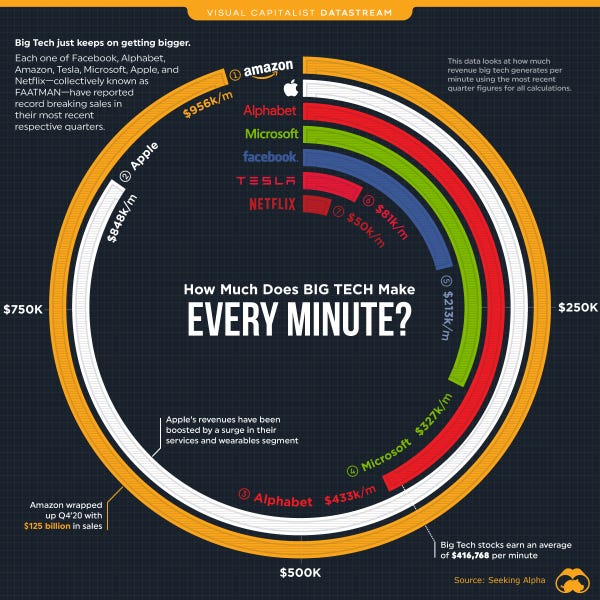
Cool Visual: How Big is FAATMAN?
Quick Clicks
That’s it for this Monday Brief. Thanks for reading, and if you think someone else would like this newsletter, please share it with your friends and followers.
Have a great week!





Please note that we at The Dispatch hold ourselves, our work, and our commenters to a higher standard than other places on the internet. We welcome comments that foster genuine debate or discussion—including comments critical of us or our work—but responses that include ad hominem attacks on fellow Dispatch members or are intended to stoke fear and anger may be moderated.
With your membership, you only have the ability to comment on The Morning Dispatch articles. Consider upgrading to join the conversation everywhere.