At least one member of the president’s legal team and other high-profile Trump supporters have alleged that Democrats are trying to “steal the election” using a super computer and accompanying software program to transfer votes to Joe Biden. Those claims have trickled down to social media posts and gone viral. One such post says that “democrat operatives used a classified supercomputer called ‘Hammer’ to steal the 2020 election.”
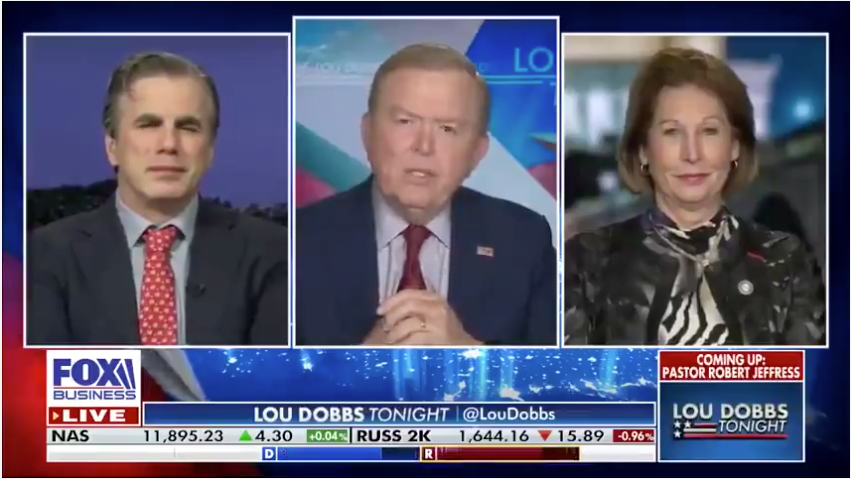
In an interview with Lou Dobbs on Fox Business News, Sidney Powell, who is on Trump’s legal team, called for an investigation into the “likelihood that 3 percent of the vote total was changed in the pre-election voting ballots that were collected digitally by using the Hammer program and the software program called Scorecard.”
According to Thomas McInerney, a retired Air Force lieutenant general, who spoke about Hammer and Scorecard on the Two Mikes podcast last week, Hammer is a “cyberwarfare tool” that was “conceived by the CIA to go against terrorists.” Scorecard, as explained by McInerney, is an application that “manipulates votes,” and, he claims, was used by Barack Obama and Joe Biden in the 2012 presidential election in order to win Florida. McInerny insists that Democrats are using this “cyberwarfare” in the current presidential election, targeting “key states” such as: Florida, Texas, Michigan, Nevada, Arizona, Pennsylvania, Wisconsin, and Georgia.
Last week, McInerney also appeared on Steve Bannon’s War Room, where he told Bannon that Hammer “was still up and running.” He claimed that the “DNC has been using this tool and it has not yet been taken down.” McInerney described Hammer as a “surveillance tool” which, he says, was modified with Scorecard, described as “a software package that changes the votes.”
These are false claims. There is no evidence to suggest that a supercomputer referred to as “Hammer” and an accompanying computer program known as “Scorecard” have been used to interfere with the results of the 2020 election.
The origins of Hammer and Scorecard can be traced back to Dennis Montgomery, a former intelligence contractor and computer programmer who claims to have developed both.
In October of this year, The American Report published a story claiming that Scorecard was “stealing votes in Florida, Georgia, Texas, Pennsylvania, Wisconsin, Michigan, Nevada, and Arizona.” The story claims that Hammer and Scorecard were “commandeered” by the Obama administration to help ensure reelection in 2012 and that Biden was using it again this time around.
The American Report story mentions that Scorecard “steals elections by tampering with the computers at the transfer points of state election computer systems…” More specifically, The American Report claims that “in Florida, one of the transfer points is VR Systems Inc.”
Douglas Jones, an associate professor of computer science at the University of Iowa, says that explanation represents a misunderstanding of the voting process.
“If you accept the idea that all of our votes somehow pass through transfer points where computer tampering could make arbitrary changes, the story holds together,” said Jones. “However, that’s not the way the system works.”
In most states, Jones explains, before a precinct relays its vote total to the county, the precinct totals are printed, usually in duplicate, and typically in the presence of observers from both political parties.
The process typically then moves as follows:
“One copy of the printout is then signed by witnesses, enclosed with the electronic results cartridge, and sealed in an envelope for hand delivery to the county election office,” said Jones. “Then, in some counties, the electronic results are transmitted by modem for quick reporting of unofficial totals, while the spare printout is posted on the wall for everyone present to look at.”
This is all to say, that interfering with election results at “transfer points” would be unlikely, according to Jones. And that’s by design.
“The fundamental problem is, there are too many witnesses from both parties, the press and the public who can see the numbers going in and compare them with the numbers the state announces,” he said. “This makes tampering at these ‘transfer points; far too easy to detect for this to be an effective attack on the election.”
Jones added that interference at these transfer points would “corrupt only the unofficial early results reported to the press, and the press are highly likely to notice the corruption.”
Lastly, according to Jones, this kind of election tampering even in states that use contractors for election administration is unlikely. “Yes, there are contractors like VR Systems that various states have outsourced election administration functions to,” he said. “Indeed, they create vulnerabilities. But no, ‘hammering’ them would not go undetected, allowing some kind of deep-state coup.”
In response to questions from The Dispatch Fact Check, Ben Martin, VR Systems Inc. COO, says the conspiracies that include his company misrepresent its role in the voting process. :
“VR Systems does not do voter tabulation and is not connected to county or state voter tabulation systems. Our company provides elections software and services to election officials who manage the voter check-in process. We also provide supervisor of elections websites and databases where voters go to check voter status, polling places. There is no connection from voter check-in to tabulation systems. VR Systems operates in Florida, some North Carolina counties and one county in Texas.”
The Hammer and Scorecard theory has been rejected by Chris Krebs, director of the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency, who, earlier this month, referred to Hammer and Scorecard as “nonsense” and “not a real thing.” He tweeted the following on November 7:
The Cybersecurity and Infrastructure Security Agency also has what Krebs describes in his tweet as “security safeguards built into elections.” On the agency’s website, there is a list of fact-checked rumors and misconceptions about the election process, to help dispel rumors such as supercomputer interference. More specifically, the rumor that “a bad actor could change election results without detection,” also included in Krebs’ tweet, is countered by CISA with the following: “Robust safeguards including canvassing and auditing procedures help ensure the accuracy of official election results.”
Montgomery, the man who claims to have “designed and built” the computer and the software involved, has a history of fraudulent claims.
According to The Daily Beast, after September 11, 2001, Montgomery’s company was paid at least $20 million by the U.S. government for “a program he claimed could detect messages to al Qaeda sleeper cells hidden in broadcasts from Qatar’s al Jazeera network.” This alleged technology, however, ended up being fake.
Court records also indicate Montgomery’s involvement in Sheriff Joe Arpaio’s legal battles. The Maricopa County Sheriff’s Office paid Montgomery $120,000 to investigate an alleged conspiracy between the Department of Justice and U.S. District Judge G. Murray Snow, who was presiding over Arapaio’s racial profiling case. Montgomery alleged that he had data showing that the Justice Department tapped Arapaio’s phone lines and was intercepting his emails. Records and court testimony indicate that detectives in the sheriff’s office determined that the data Montgomery delivered was “bogus.” A New York Times article about Arpaio’s case states that, “When Judge Snow suggested that the materials provided by Mr. Montgomery were ‘junk, [Maricopa Sheriff’s Office] Deputy Sheridan and Sheriff Arpaio agreed.”
If you have a claim you would like to see us fact check, please send us an email at factcheck@thedispatch.com. If you would like to suggest a correction to this piece or any other Dispatch article, please email corrections@thedispatch.com.
This fact check is available at IFCN’s 2020 U.S. Elections FactChat #Chatbot on WhatsApp. Click here for more.






Please note that we at The Dispatch hold ourselves, our work, and our commenters to a higher standard than other places on the internet. We welcome comments that foster genuine debate or discussion—including comments critical of us or our work—but responses that include ad hominem attacks on fellow Dispatch members or are intended to stoke fear and anger may be moderated.
With your membership, you only have the ability to comment on The Morning Dispatch articles. Consider upgrading to join the conversation everywhere.