On June 3, MyPillow CEO and Donald Trump supporter Mike Lindell released a third documentary claiming that Trump won the 2020 presidential election. The latest, Absolutely 9-0, follows Lindell’s previous two documentaries, Absolute Proof and Absolute Interference, both of which we have previously fact checked. All three claim, despite a lack of evidence, that the 2020 election was stolen from Trump.
Lindell claims that Absolutely 9-0 will show why he has been “100% sure that when this gets before the Supreme Court it’s going to be 9-0,” adding that “this was 100% an attack by China on our country through these machines.” In mentioning “these machines,” Lindell is referring to Dominion Voting Systems machines that were used in parts of 28 states in the 2020 election. Dominion was the subject of many false claims about election fraud.
Lindell was sued by Dominion Voting Systems in February for his baseless public statements about the company’s involvement in “stealing the election” from Trump. In April, Lindell filed a countersuit against Dominion, claiming that Dominion’s goal is to “silence debate” and that the suit interferes with free speech. Earlier this month, Lindell filed another lawsuit against both Dominion and Smartmatic, another company that provides voting technology services and was subject to false claims during the election, “to stop electronic voting machine companies from weaponizing the litigation process to silence political dissent and suppress evidence showing voting machines were manipulated to affect outcomes in the November 2020 general election.”
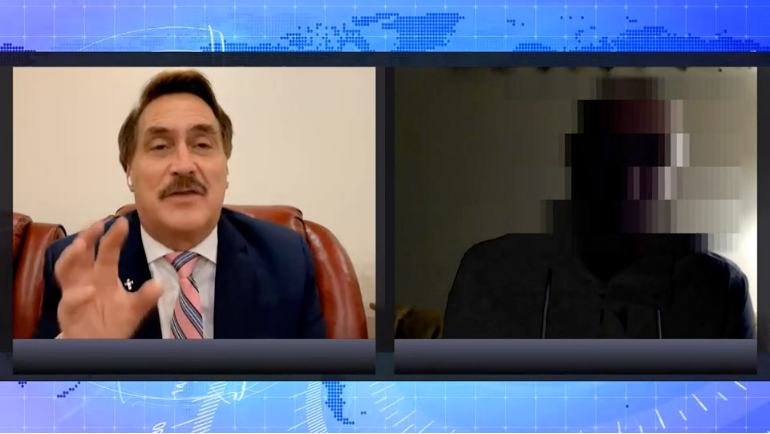
A portion of Absolutely 9-0 is centered on Lindell’s interview with an anonymous “cybersecurity expert” with “over 20 years experience working in both the private sector and with government law enforcement.” The “expert” and Lindell then present what the “expert” calls the “raw encrypted data” that he claims are “PCAPs.”
First, some context on PCAPs. Kevin Skoglund, president and chief technologist of Citizens for Better Elections, a nonpartisan nonprofit described as being “dedicated to promoting election security and efficiency in Pennsylvania,” explained in an interview with The Dispatch Fact Check that PCAP, or packet capture, is a standard networking way that you can view traffic over the internet. “Traffic over the internet is sent as packets of information,” he said. “They aren’t encrypted, necessarily, but they are encoded, because they don’t need to be human-readable while they’re in transit.”
In an email to The Dispatch Fact Check, Douglas Jones, an associate professor of computer science at the University of Iowa, further explained PCAP using an email as an example to understand the concept more thoroughly.
“When I hit ‘Send’ on my screen, my web browser plus the Internet software on my computer encrypts it and then splits it up into a bunch of packets,” he explained. “Each packet gets a serial number and a header and trailer attached to it.” The header, he said, would include the destination address, which in this example is a cloud data center run by Microsoft (email service provider). The packet, Jones continued, would then get handed off to his internet service provider, CenturyLink, which he noted, has many connections to other internet companies.
“Packets are sent preferentially to the highest speed link going in the right direction, but the routing algorithms worry about congestion,” said Jones. “The net result is that the packets are sent out in a shotgun blast, and the different packets are likely to take a variety of different routes.”
The packets, he continued, are reassembled and then decrypted to get at the email message and the Microsoft servers try to send that message onward to the email service provider. To accomplish this, “it encrypts the message and breaks it down into packets again and shotguns them out across the Internet. Your email service provider reassembles the packets, decrypts it, figures out that it’s for you, and when you connect to your email service, it gets encrypted, split up again and shotgunned to the PC on your desktop, which reassembles it and puts it up on your screen.”
Jones further explained that because most of the routers and other computers on the path from you to Microsoft have multiple connections, you’d only be able to see some of the packets of the email.
“Suppose this email is divided into 12 packets and you get only 7 of them. The email is encrypted (and the encryption used on the Internet is very good, but certainly not perfect). You really can’t decrypt the email until you get all the packets,” he said.
Going back then to Lindell, Skoglund pointed out a number of issues with his claim about his supposed PCAPs, calling his assertions “technically incoherent and wrong in several ways.”
Here’s the basic idea of Lindell’s claim, according to Skoglund: Lindell is saying he has a team of experts who collected internet traffic going from computers in foreign countries to U.S. counties, where foreign computers contacted computers that are responsible for providing election results, all pointing to data that shows there was a successful system intrusion that changed votes.
First of all, if Lindell’s claim were correct, it would be remarkable that he was the only one to detect the supposed system intrusion. “An extraordinary claim needs extraordinary evidence,” Skoglund said, “and they provide little evidence at all.” Also, it’s important to note that Lindell’s “expert” is anonymous, so we have neither the name nor credentials of this person.
Skoglund then broke down why Lindell’s evidence, which at first appears as semi-illegible data moving down the screen, doesn’t hold up.
As Skoglund points out, “it’s not so easy to just observe internet traffic” and access to this information is not readily available to just anyone. Lindell, of course, doesn’t claim to have access and does not say how he might have gotten access, if he does. It wouldn’t be impossible to get this type of access, but it’s difficult, Skoglund said. “They owe us an explanation for how they are able to see what they claim to see.”
Jones also noted why it would be so difficult to access this information. Jones mentioned that Lindell is claiming that his PCAPs show exactly how many votes were stolen through these internet transactions, but his evidence doesn’t hold up. “The only way to capture packets addressed to and from all those different election offices around the country would be to have the resources of the NSA [the National Security Agency],” he said. “That is, if his data is real and not entirely fictional, the only source would be someone inside the NSA providing it. This would be a felony violation of U.S. law—actually a compound felony.”
Additionally, Lindell’s data, or what he claims to be PCAPs, Skoglund notes, is old. It’s the same data used in Lindell’s two previous documentaries. The data, which again purports to prove a connection between a computer in a foreign country and a computer that is election related, doesn’t prove foreign interference and doesn’t represent PCAPs. As the Washington Postreported, the data appears to actually be voter information from Pennsylvania, which as the Washington Post notes, can be purchased from the state.
Furthermore, as Skoglund notes, PCAPs are not viewed in hexadecimal digits (the numbers 0 through 9 and the letters A through F), which is how Lindell’s supposed PCAPs appear on screen. “Nobody looks at PCAPs that way,” Skoglund said. And, again as the Washington Post mentioned the data is just voter data represented in hexadecimal digits.
What’s more, Lindell told Lead Stories that the data presented isn’t actually an election PCAP file, and as Lead Stories reported: “he [Lindell] claimed he had the actual election pcap files in his possession and that he did not show them in the video for ‘security.’”
Jones also pointed out a number of flaws with Lindell’s supposed PCAP evidence. “He claims to not only know who sent and who received the packets, but also what those packets meant,” said Jones. “That means that his source has decrypted the traffic. Modern cryptography is really strong. The NSA and the FBI have a very hard time breaking codes used routinely for such things as encrypted email and web service.”
Additionally, as Jones points out, Lindell says that in certain cases, PCAPs show evidence of specific numbers of votes stolen. “That requires understanding the mechanism of vote theft,” he said. “It’s very hard for me to imagine a message, in a single packet, saying ‘steal 10 votes from Trump.’”
It’s worth mentioning again, that although these films haven’t received a significant amount of attention in the mainstream media, reporters have noted that voters have asked about Lindell’s voter fraud films.
If you have a claim you would like to see us fact check, please send us an email at factcheck@thedispatch.com. If you would like to suggest a correction to this piece or any other Dispatch article, please email corrections@thedispatch.com.





Please note that we at The Dispatch hold ourselves, our work, and our commenters to a higher standard than other places on the internet. We welcome comments that foster genuine debate or discussion—including comments critical of us or our work—but responses that include ad hominem attacks on fellow Dispatch members or are intended to stoke fear and anger may be moderated.
With your membership, you only have the ability to comment on The Morning Dispatch articles. Consider upgrading to join the conversation everywhere.