Quick Note: I’m traveling for work this week so I’m unable to record the audio version of this week’s newsletter. Sorry about that, but we should be back in action next week.
The Vandenberg Coalition
What’s New: I’ve joined the advisory board of an organization advocating that a strong and proud US foreign policy best serves the interests of the American People. You can read our official announcement here in the Wall Street Journal.
Why This Matters: The US faces significant threats — including revisionist powers, the spread of nuclear, chemical, and biological weapons, and disruptive emerging technologies — all made more perilous by renewed great power competition and the threats posed by the Chinese Communist Party (CCP).
Key Points: The Vandenberg Group has six orienting principles:
-
We believe that American security depends on American leadership. The United States must remain the most powerful nation and influential leader in the world.
-
We believe that a strong America is a safe America. A strong national defense is essential to protect the vital interests of the American people and to deter aggression and hostility abroad.
-
We believe that strategic cooperation serves American interests. Robust alliances among sovereign nations and the strategic use of multilateral institutions can preserve and advance US interests. Nations joined in common cause, not supranational global government, are the foundation of international cooperation and peace.
-
We believe that economic security is essential to national security. We believe in free and fair trade to advance the prosperity and security of the American people. US trade and investment agreements should benefit workers and families in the United States. America must sustain its defense industrial base, lead efforts against predatory economic practices, and promote respect for the rules of international trade and commerce.
-
We believe in a proud American foreign policy. The strategic pursuit of American principles advances American security. We believe that the United States is among the greatest forces for peace, freedom, and justice in the world. Our nation has a noble heritage and unrivaled moral strength. We believe in a proud American foreign policy that champions American values without apology.
-
We believe in American leadership of, by, and for the American people. The American people are the ultimate arbiters of U.S. foreign policy. The foreign policy of the United States should be responsive to the interests and principles of Americans not just in Washington, but all across our country.
What I’m Thinking: You’re probably wondering, “Why ‘Vandenberg’”?
-
The Vandenberg Coalition derives its name from the late United States Senator from Michigan, Arthur Vandenberg, who served in the Senate from 1928 until his death in 1951.
-
Originally an isolationist, Vandenberg ultimately became a leading advocate for strong American leadership after the Japanese attack on Pearl Harbor during World War II.
-
He worked across party lines to protect U.S. national security interests and promote candid debate on foreign policy.
-
The Vandenberg Coalition embodies several core aspects of Arthur Vandenberg’s life and values, including a bipartisan, patriotic, and collaborative spirit; sincere commitment to advancing the interests of the American people; and advocacy for a strong and realistic U.S. foreign policy.
-
You can find out more here. Stay tuned for new updates and policy work.
Ransomware Report Urges Immediate Action
What’s New: A new report from the Institute for Security and Technology argues that “Ransomware attacks present an urgent national security risk around the world” and offers a series of recommendation for engaging this challenge.
Why This Matters:
“In 2020, thousands of businesses, hospitals, school districts, city governments, and other institutions in the U.S. and around the world were paralyzed as their digital networks were held hostage by malicious actors seeking payouts. The immediate physical and business risks posed by ransomware are compounded by the broader societal impact of the billions of dollars steered into criminal enterprises, funds that may be used for the proliferation of weapons of mass destruction, human trafficking, and other virulent global criminal activity.”
Key Points:
-
Ransomware has blown up over the last four years and not only threatens individual and corporate financial security, but also risks human life and national security.
-
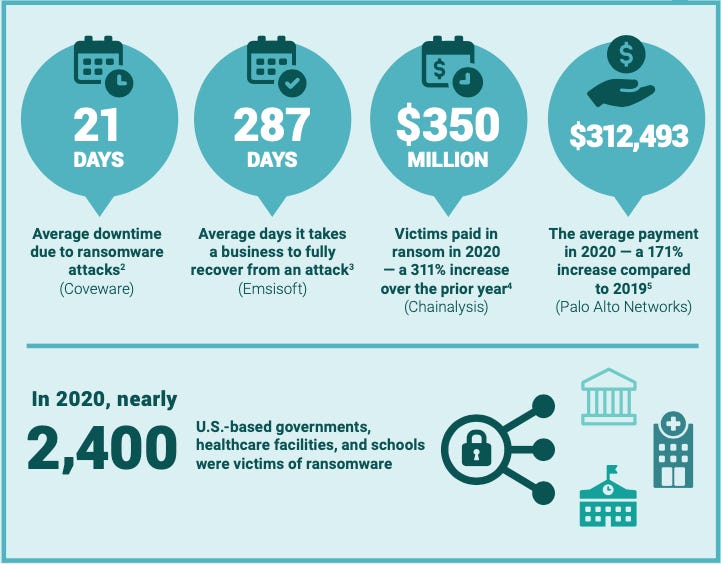
In 2020, nearly 2,400 U.S.-based governments, healthcare facilities, and schools were victims of ransomware, according to the security firm Emsisoft.
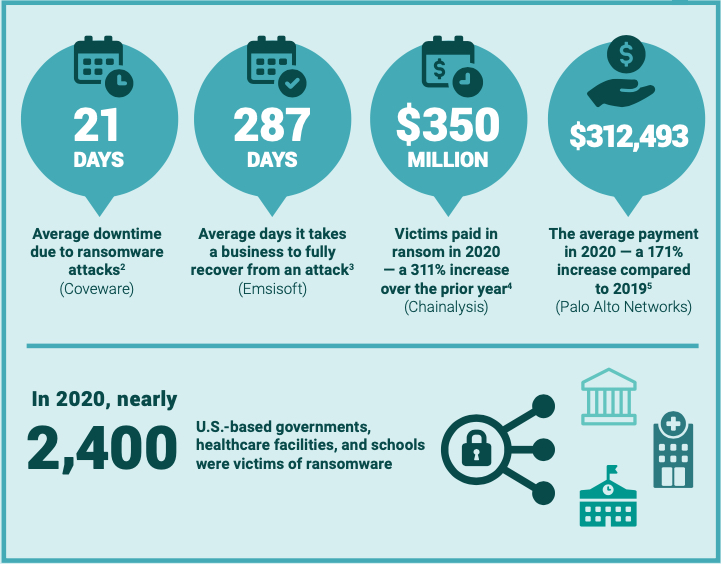
Here are the report’s five priority reccomendations:
-
Coordinated, international diplomatic and law enforcement efforts must proactively prioritize ransomware through a comprehensive, resourced strategy, including using a carrot-and-stick approach to direct nation-states away from providing safe havens to ransomware criminals.
-
The United States should lead by example and execute a sustained, aggressive, whole of government, intelligence-driven anti-ransomware campaign, coordinated by the White House. In the U.S., this must include the establishment of 1) an Interagency Working Group led by the National Security Council in coordination with the nascent National Cyber Director; 2) an internal U.S. Government Joint Ransomware Task Force; and 3) a collaborative, private industry-led informal Ransomware Threat Focus Hub.
-
Governments should establish Cyber Response and Recovery Funds to support ransomware response and other cybersecurity activities; mandate that organizations report ransom payments; and require organizations to consider alternatives before making payments.
-
An internationally coordinated effort should develop a clear, accessible, and broadly adopted framework to help organizations prepare for, and respond to, ransomware attacks. In some under- resourced and more critical sectors, incentives (such as fine relief and funding) or regulation may be required to drive adoption.
-
The cryptocurrency sector that enables ransomware crime should be more closely regulated. Governments should require cryptocurrency exchanges, crypto kiosks, and over-the-counter (OTC) trading “desks” to comply with existing laws, including Know Your Customer (KYC), Anti-Money Laundering (AML), and Combatting Financing of Terrorism (CFT) laws.
What I’m Thinking: Ransomware is big and it is only getting bigger. The only thing keeping this problem from being a total nightmare is the bad guys’ creativity and willingness — not our cyber defenses. The report is a good initiation for anyone wanting to understand the threat better, but I’ll add a little color to its first and second recommendations: the US intelligence/military enterprises should specifically be tasked to identify, deter, disrupt, and dismantle foreign ransomware attackers and their networks. These attacks should be treated as cyberterrorism and nation states who enable or harbor these attackers should be engaged accordingly. The reality is that we’re not going to be able to deny this capability to people who want to cause havoc, and so we must do what is necessary to make these attacks so costly, so painful for the bad guys, that they decide the rewards aren’t worth the risk.
Digital Exhaust Is Giving Away Military Secrets
What’s New: A Wall Street Journal article details how mobile phones can be used to track US soldiers.
Why This Matters: This again raises important questions about how to protect American intelligence personnel, military service members, and civilians when highly detailed commercial data from phones and other devices can be purchased by anyone — including America’s enemies.
Key Points:
-
In 2016, a company called PlanetRisk was building a software prototype for the Department of Defense when they discovered that they could easily track American military personnel.
-
The original software was supposed to use mobile games, weather apps, and other digital data to monitor refugee travel between Syria, Europe, and the US. But it soon became clear that the “digital exhaust” from US military phones was also being collected and commingled with this data.
-
When PlanetRisk traced telephone signals from US bases to a Syrian cement factory in 2016, it hadn’t been disclosed publicly that the factory was being used as a staging area for American and allied forces. Moreover, the company could monitor the movements of US troops while they were on patrol—a serious operational security risk that opened units up to being targeted by enemy forces.
The Department of Defense “is aware of the risks posed by geolocation tracking capabilities, including via commercial data, and issued policy on the use of geolocation-capable devices and applications in the summer of 2018,” said Pentagon spokeswoman Candice Tresch. “[A DoD] policy, and its implementing risk guidance, protects DoD personnel and operations while still allowing flexibility to benefit from geolocation capabilities in certain low-risk situations,” the spokeswoman said.
What I’m Thinking: Last year, the NSA issued a bulletin urging military and intelligence personnel to turn-off location tracking and other data collection on their phones.
“Location data can be extremely valuable and must be protected,” the NSA bulletin warned. “It can reveal details about the number of users in a location, user and supply movements, daily routines (user and organizational), and can expose otherwise unknown associations between users and locations.”
Likewise, the FBI has a 300-page “Digital Exhaust Opt Out Guid” that explains how to limit digital tracking.
Neither of these actions have meaningfully reduced the threat. Throughout the cybersecurity community it is now clear that depending on users to secure themselves is the best way to ensure that we remain vulnerable. Instead, we need a national “moonshot” effort on security and encryption technologies that will allow data to be used while never being exposed (i.e., homomorphic encryption). Likewise, we need to do obvious stuff like prevent foreign nations from simply purchasing mobile data on Americans.
Quick Clicks
-
China’s space station launch might cost lives on the ground.
-
A tech company tried to limit what employees talk about at work … It didn’t go well.
-
NASA suspends SpaceX’s $2.9 billion moon lander contract after rivals protest.
-
Researchers warn: AI algorithms can influence people’s voting and dating decisions.
-
The world’s first robotics venture factory is on ‘robot island’ In Denmark.
That’s it for this Monday Brief. Thanks for reading, and if you think someone else would like this newsletter, please share it with your friends and followers. Have a great week!






Please note that we at The Dispatch hold ourselves, our work, and our commenters to a higher standard than other places on the internet. We welcome comments that foster genuine debate or discussion—including comments critical of us or our work—but responses that include ad hominem attacks on fellow Dispatch members or are intended to stoke fear and anger may be moderated.
With your membership, you only have the ability to comment on The Morning Dispatch articles. Consider upgrading to join the conversation everywhere.